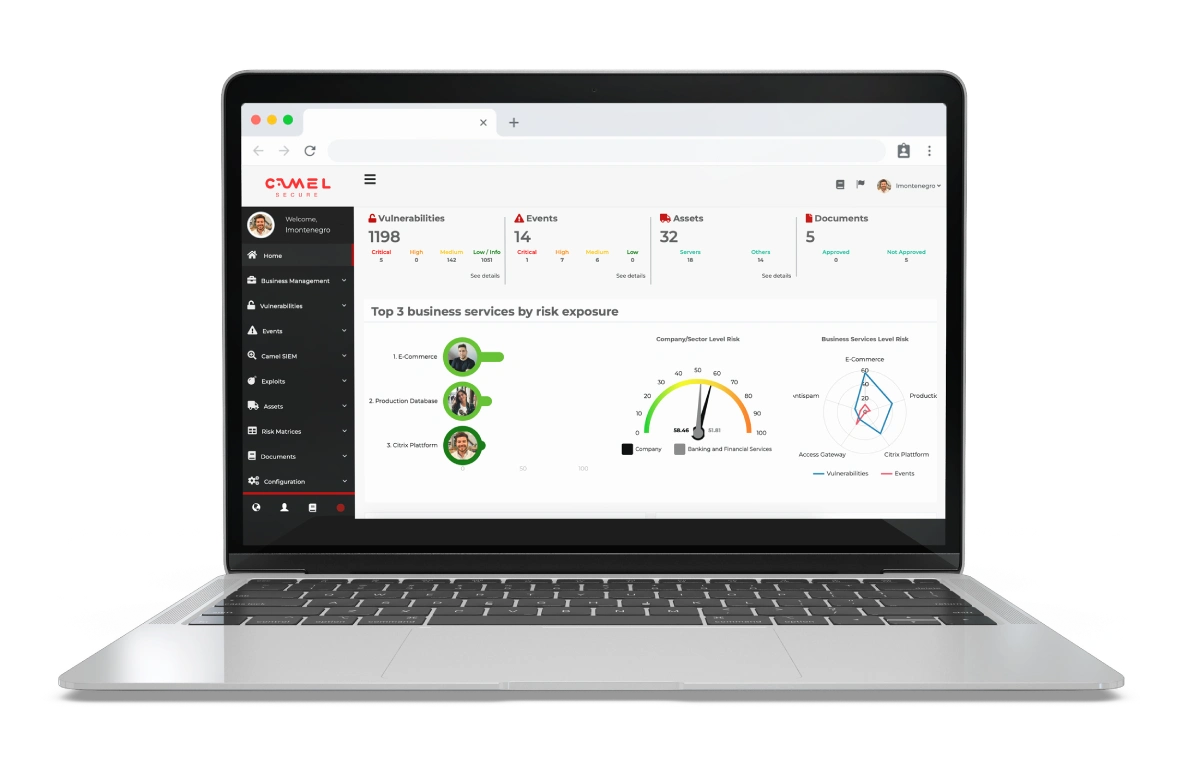
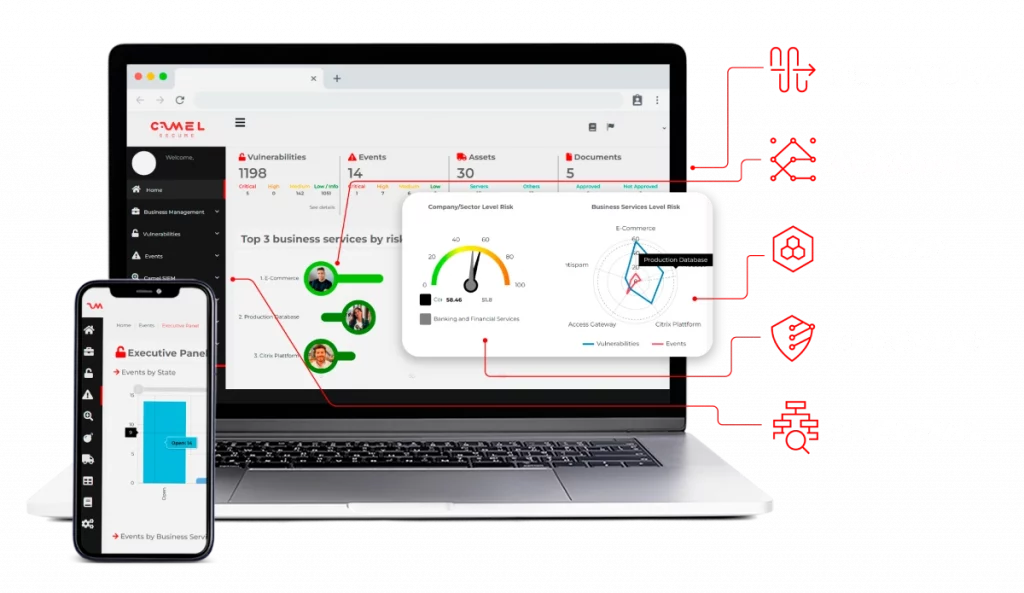
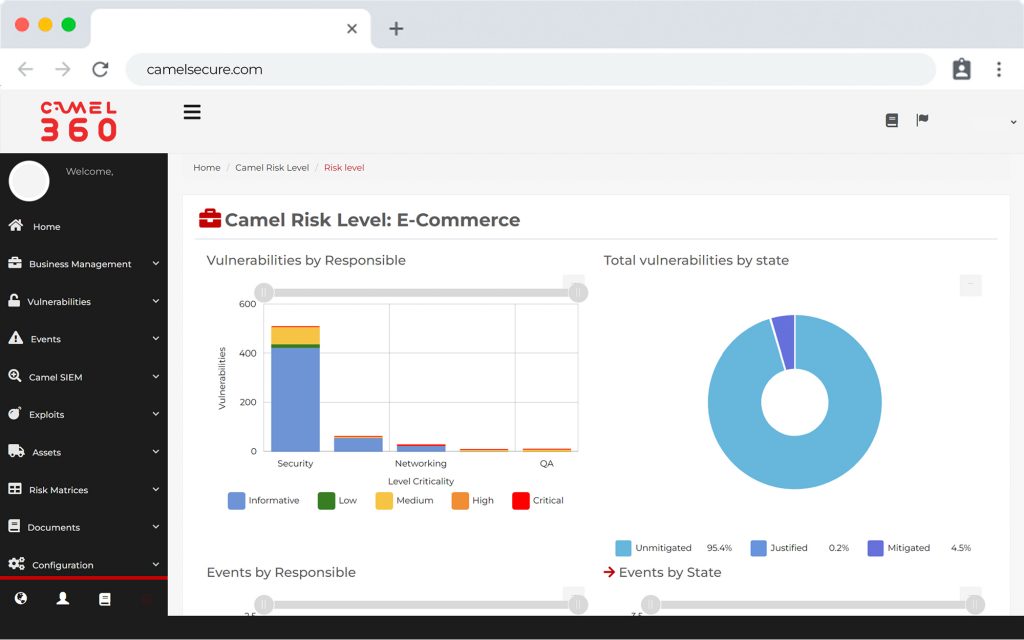
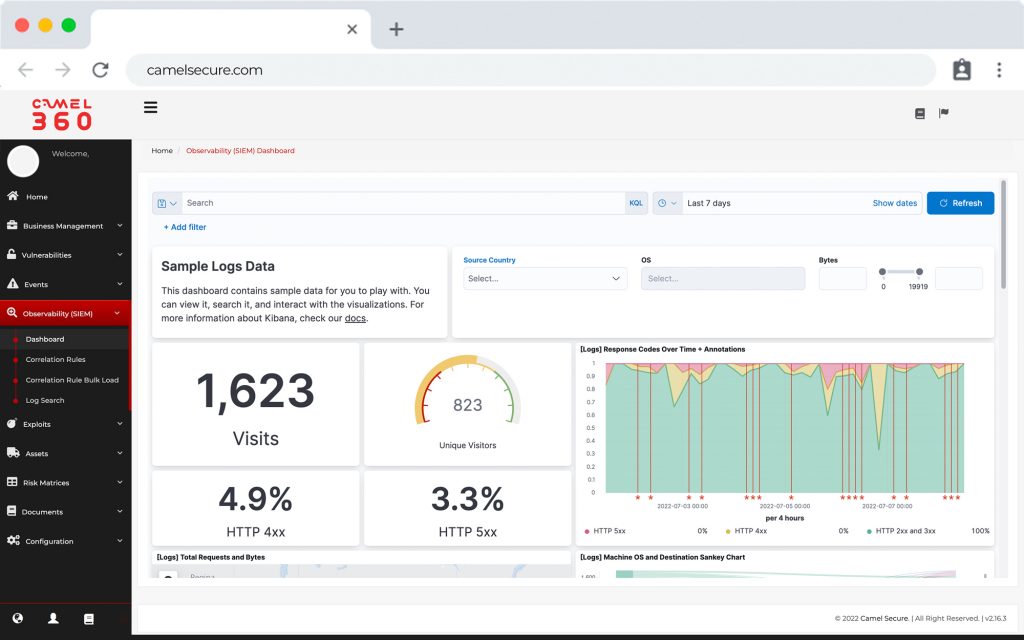
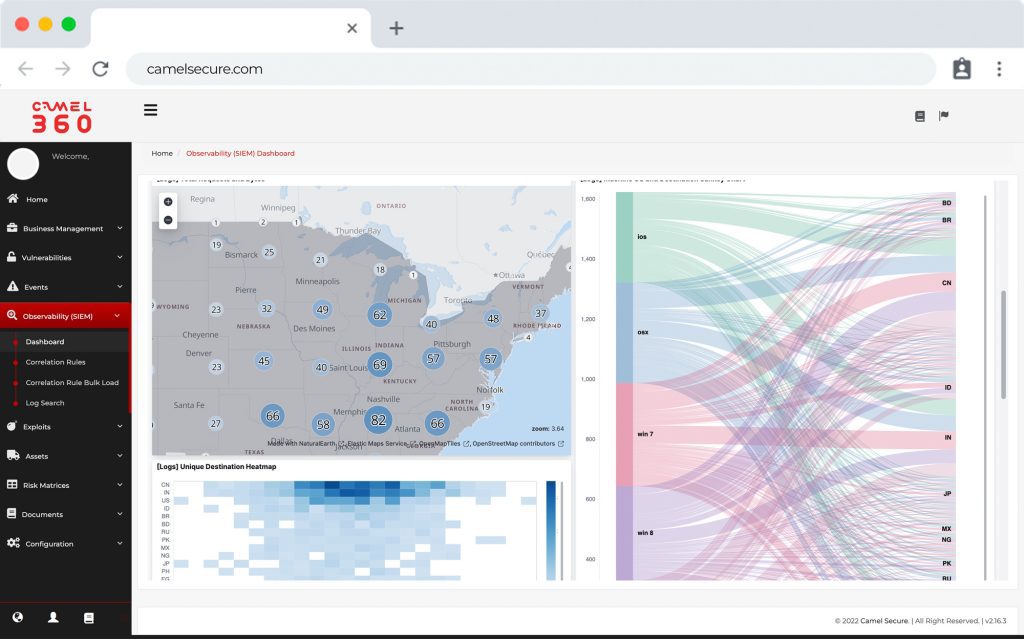
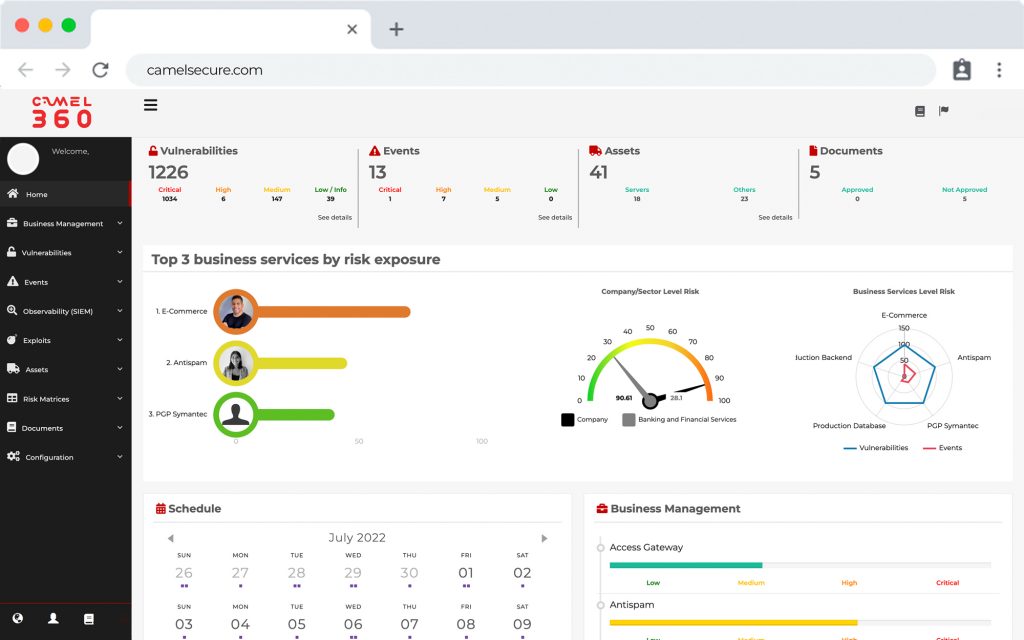
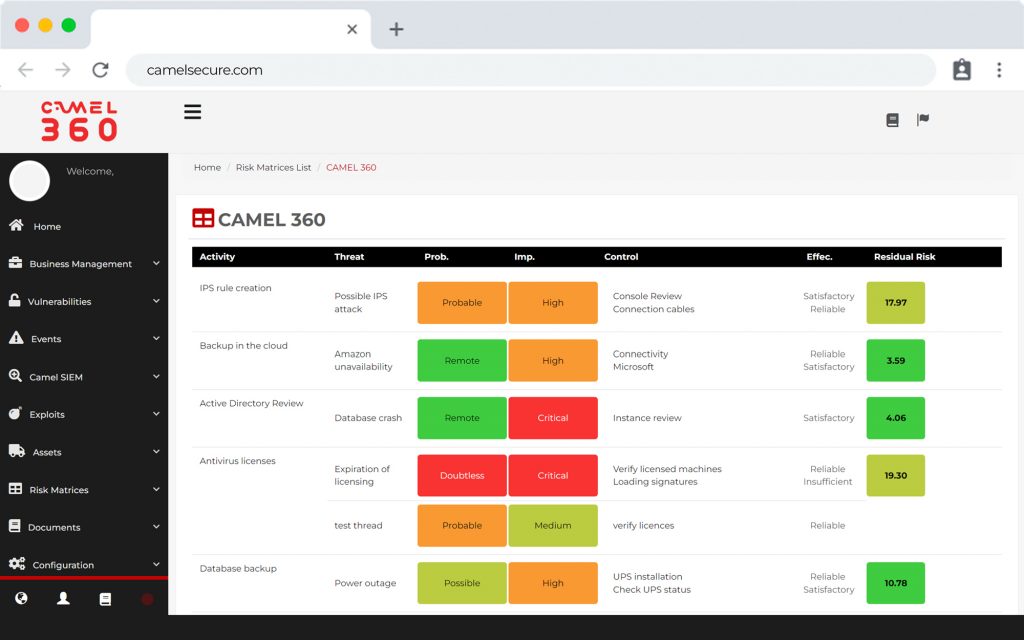
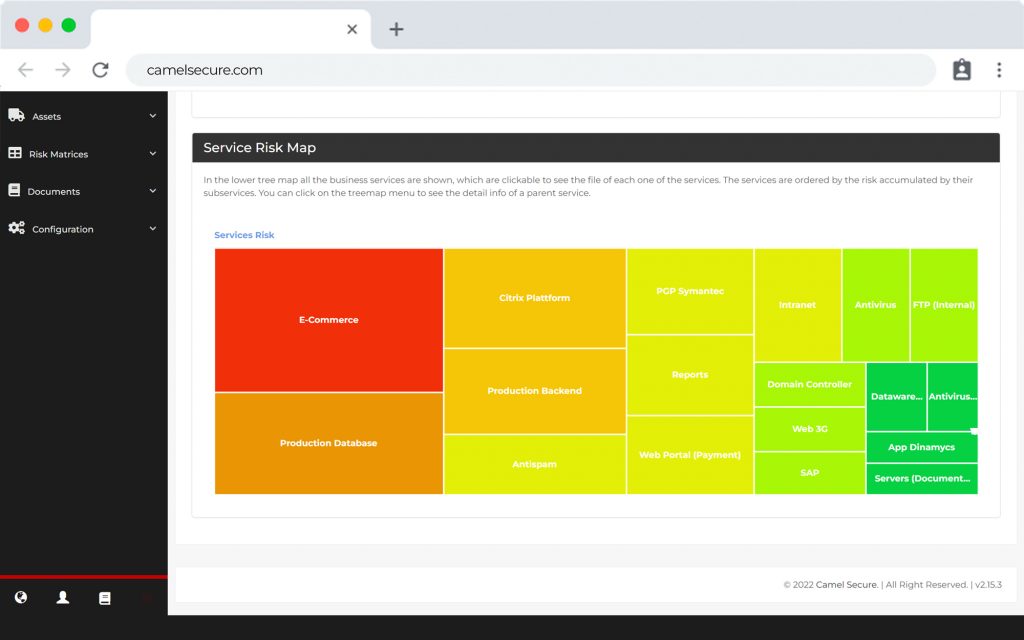
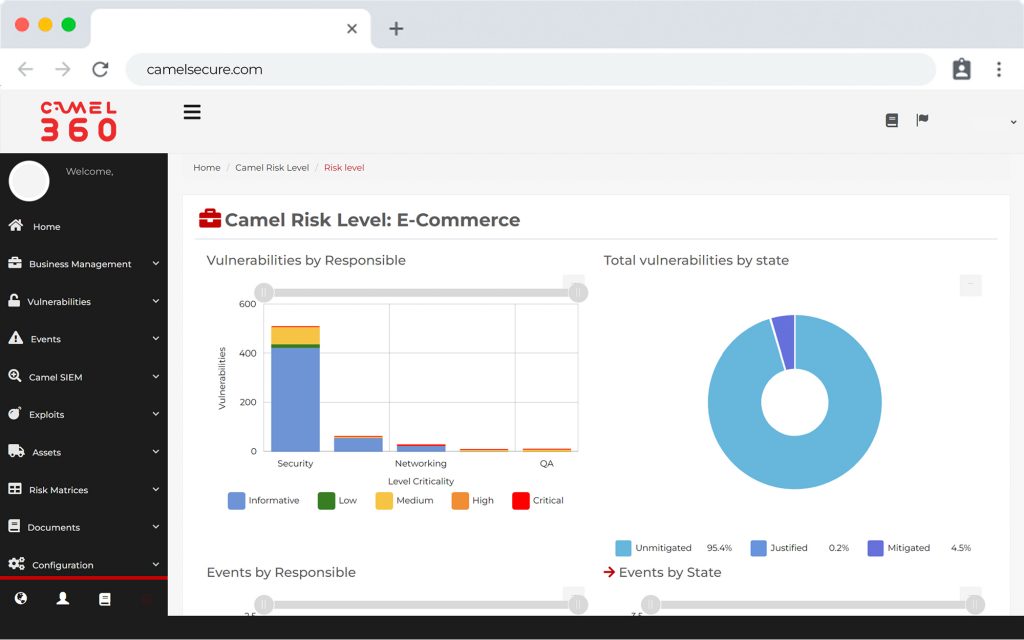
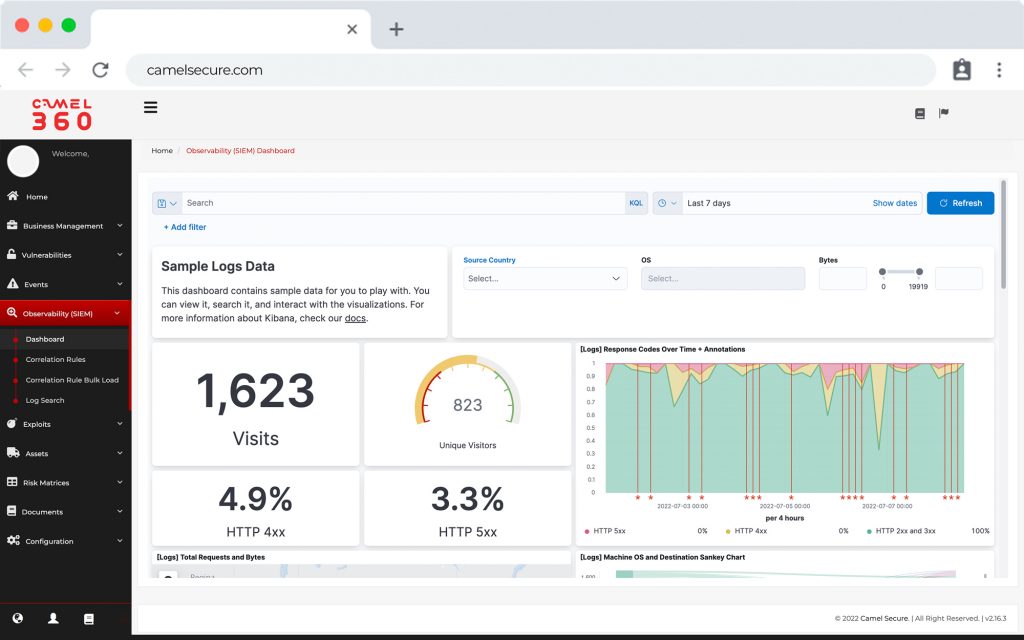
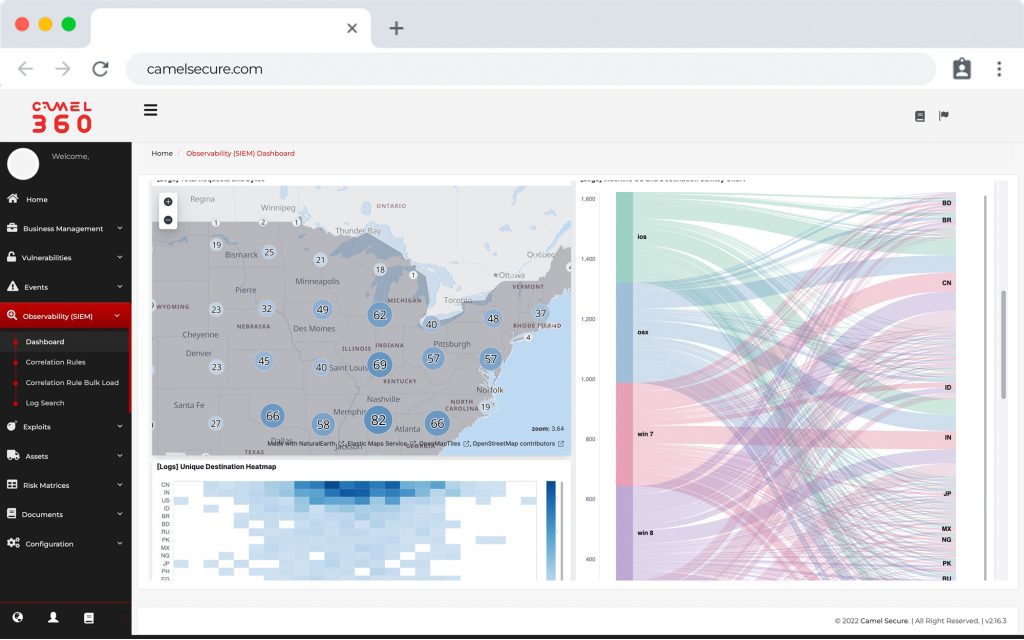
SIEM y Log Management
- Event Correlation
- Log Management
- 12 months log retention
Asset Discovery
- API-powered asset discovery
- Network asset discovery
- Software and services discovery
Extension Of Your Team
- Constant communication
- Guided team response
- Expert security recommendations
Integration With Existing Systems
- Accept logs from most devices
- Powerful integration with many brands
- Supports cloud services and enterprise tools
Vulnerability Assessment
- Network Vulnerability Scanning
- Cloud Vulnerability Scanning
- Host-based Intrusion
Intrusion Detection
- loud Intrusion Detection
- Host-based Intrusion Detection (HIDS)
- Edge-to-end user tracking
Behavioral Analysis
- Asset access logs - Cloud access and activity logs - AWS VPC Flow monitoring - VMware ESXi Access logs
Endpoint Detection And Response
- File Integrity monitoring
- Continuous endpoint monitoring
- Proactive querying and threat detection