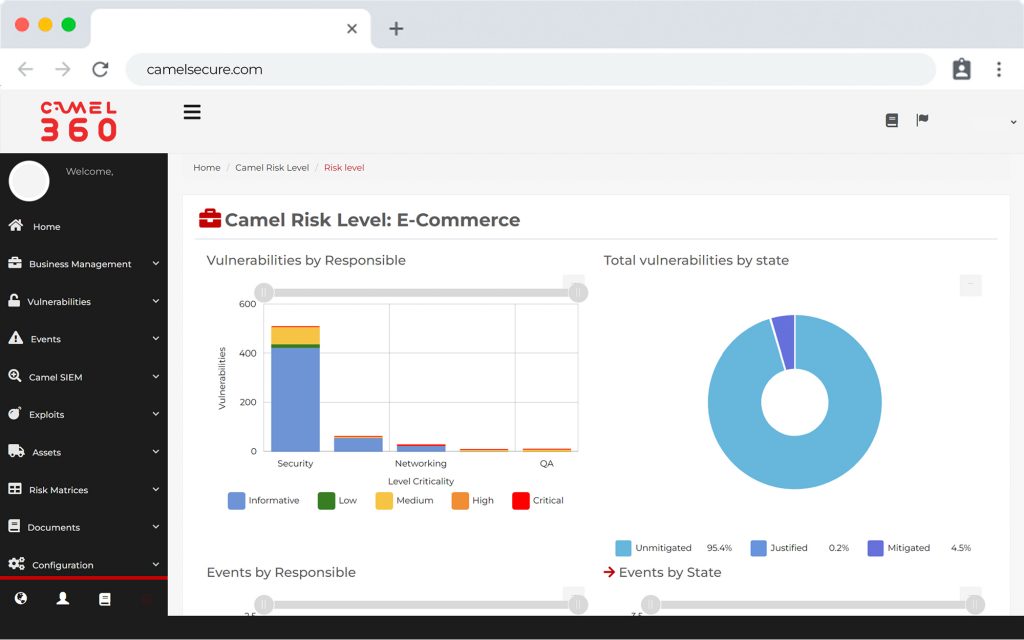
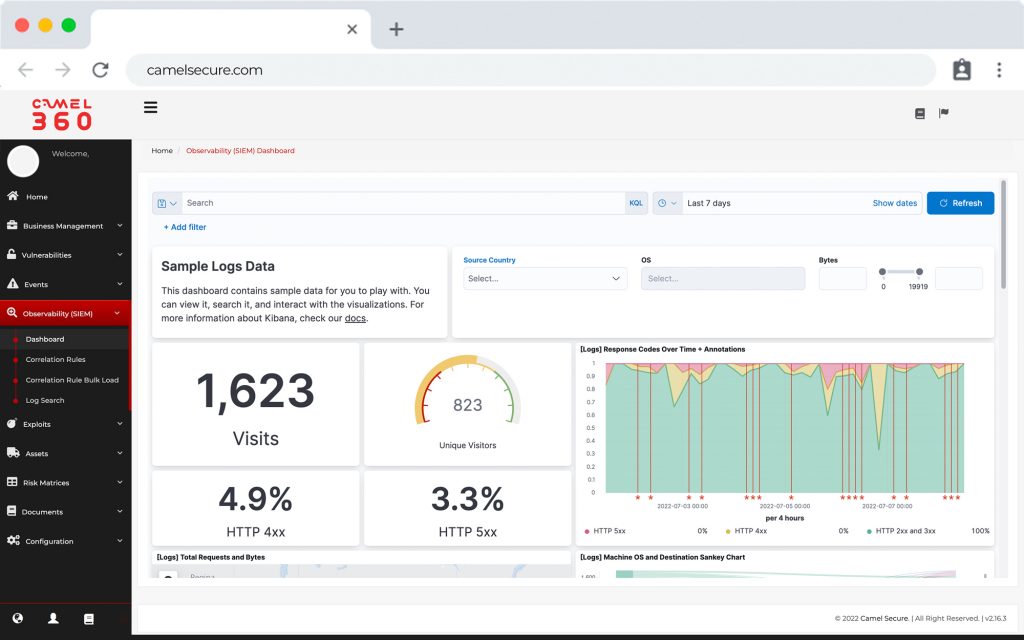
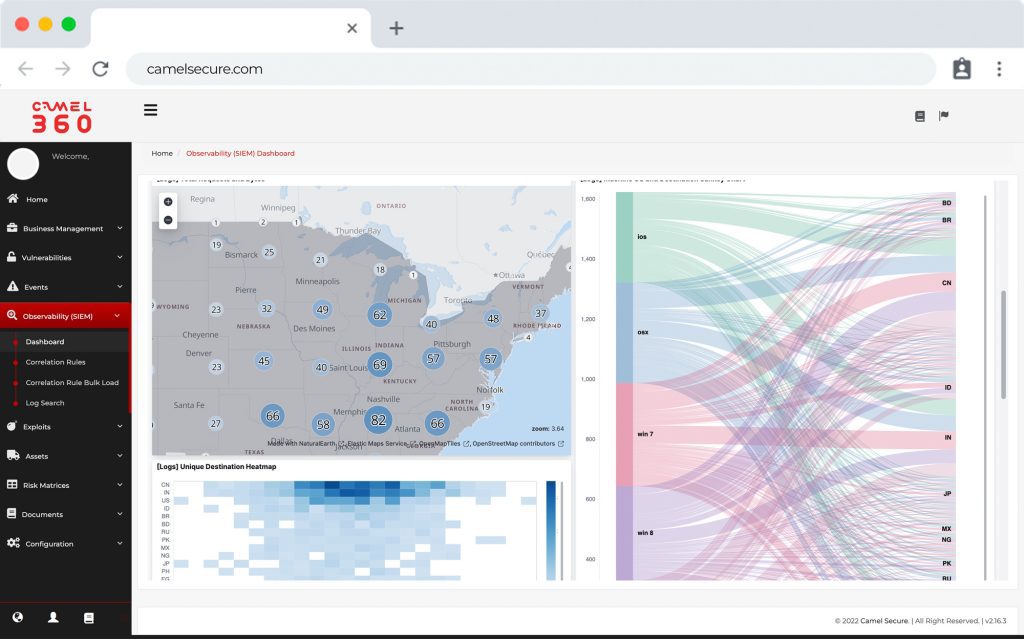
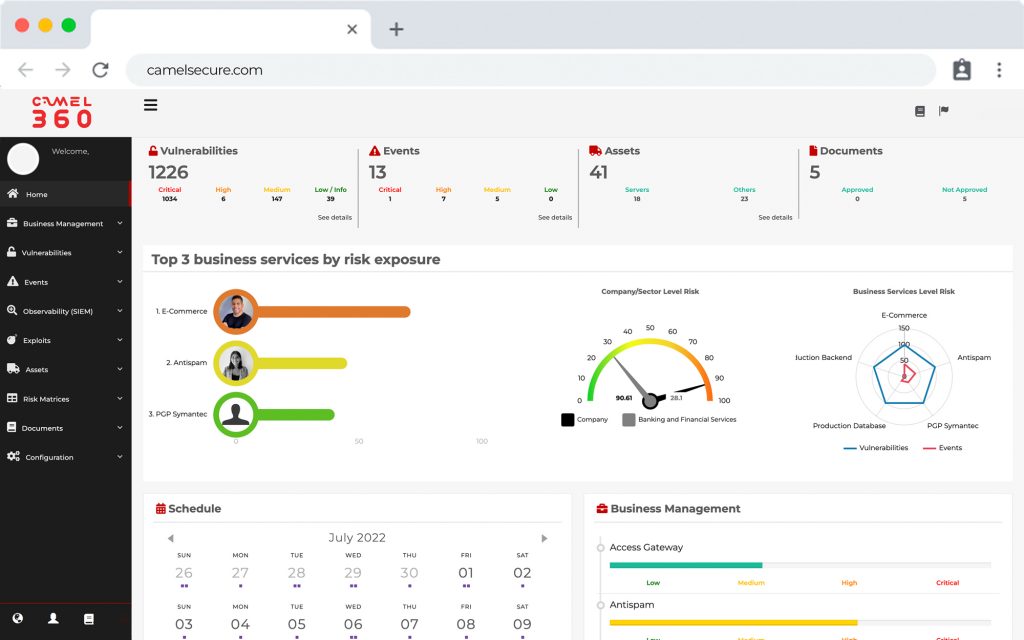
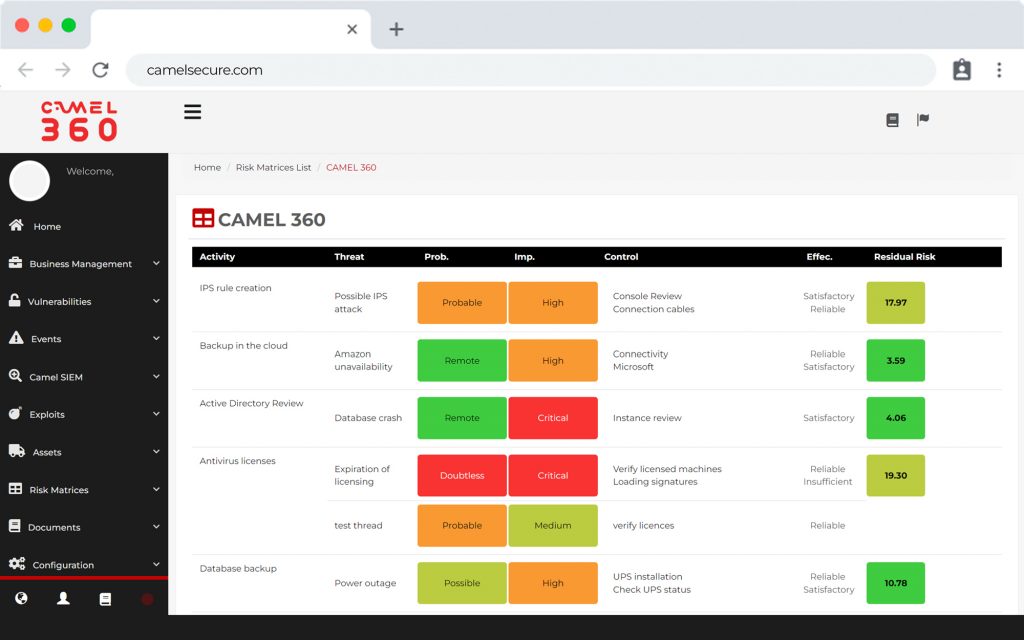
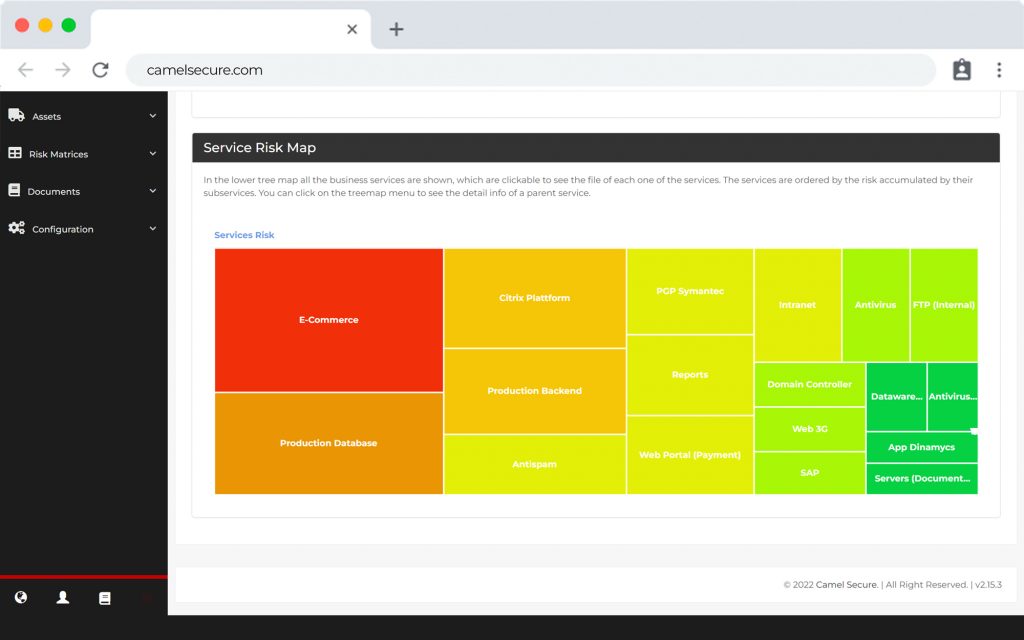
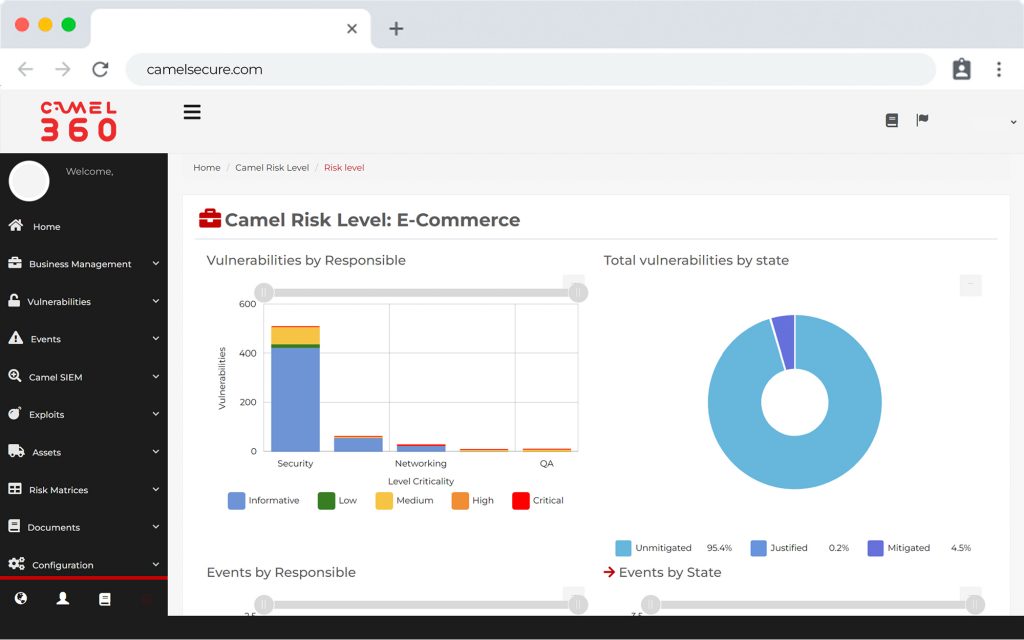
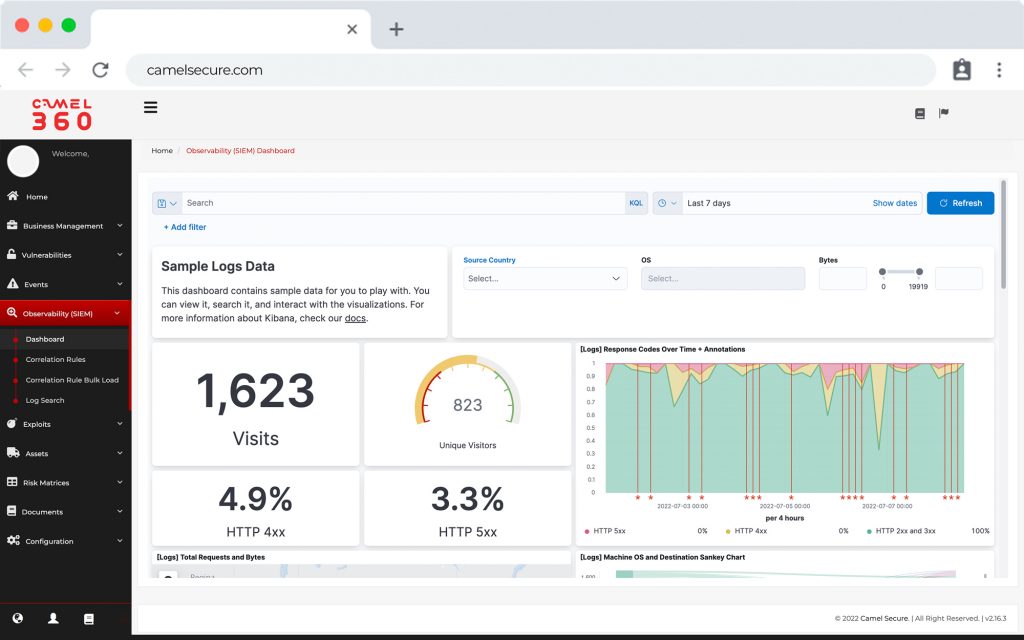
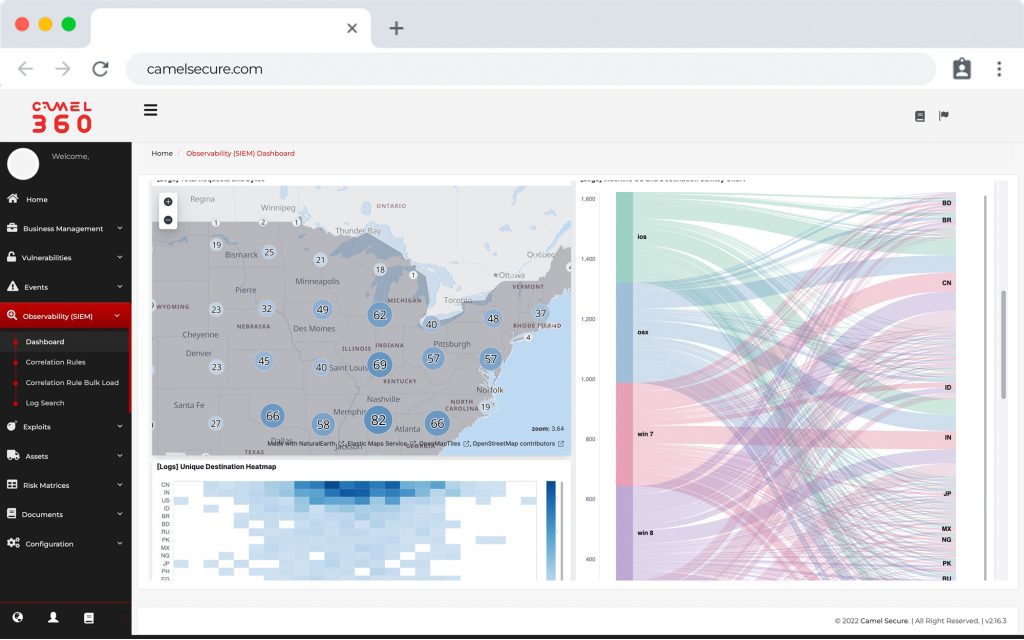
COR, much more than a SIEM, is the preferred choice for teams that need security monitoring for critical infrastructure.
- COR extends the capabilities of your Security Log Management on an unprecedented scale in the cloud or on-premises, providing additional functions for threat, detection, investigation and response (TDIR). Our observability software allows you to work with our SIEM (ELK) COR which includes comprehensive alert and case management, over 10,000 pre-built correlations, integrated threat intelligence and powerful dashboard capabilities. The solution offers analysts breakthrough speed, with the ability to process more than 1 million events per second (EPS) on a sustained basis and the ability to search through multiple years of data, whether hot, warm or cold, in a matter of seconds. We have a hybrid technology that fits your storage needs.
Complete collection of records
Collect data securely, either from local or cloud sources, at a significant scale through a unified interface. Each raw record is parsed to become a security event, where named fields are identified and normalized in a standard format, facilitating rapid analysis and consolidated security context. Our wizard simplifies the creation of custom parsers from new log sources or templates, streamlining the development, deployment and error-free management of parsers. In addition, it processes events at more than 1 million per second (EPS) on a sustained basis.
Our platform supports more than 200 products, offering multiple transport methods, such as API, agent, syslog and SIEM data lake. In addition, we integrate 25 cloud security products, 15 SaaS productivity applications, and 18 cloud infrastructure products. With an impressive set of more than 10,000 pre-built log analyzers, we offer a comprehensive solution for security data collection and analysis needs.

Security log management at scale in the cloud or on-premise
-
Security log management benefits from a cloud-scale architecture, enabling data ingestion, analysis, storage and search at impressive speeds. A key feature of COR is its search function, a unique interface that allows analysts to explore hot, warm, cold and frozen data with equal speed. We eliminate the need to import or wait for historical data restoration and processing, with no learning curve: analysts do not have to familiarize themselves with a proprietary query language.
In addition, COR enables the rapid creation of powerful visualizations from analyzed log data on the fly. You can build a dashboard in a minute using 12 different types of pre-designed charts. We simplify the process so analysts can focus on getting valuable information without hassle.
Ticketing Manager
-
Advance toward the security results you need by closing critical gaps. Thoroughly understand the coverage and configuration of your data sources to discover precise actions. Quickly assign findings to your teams with our ticketing manager and strengthen your security posture through visualizations of recommended information, event streams and analysis configurations. Plus, enjoy a powerful and affordable log management solution designed exclusively for security. Your teams will adopt it easily, without facing a steep learning curve. We also have the ability to integrate with the ticket manager of your choice.
Advanced correlation capabilities
-
Transform your searches into effective threat search rules with a single click. Well-designed correlation rules enable you to identify a wide variety of behaviors and events. Easily write, test, publish and monitor hundreds of custom correlation rules, even specifying higher criticality for those related to Threat Intelligence Service activities.
10,079
Predesigned log analyzerss
As data is entered, it is subjected to analysis using an extensive array of more than 10,000 pre-built log analyzers. In addition, they are enriched with contextual information from both commercial and open source threat intelligence sources.
1,000,000+
Event per second
We guarantee fast processing in log ingestion, maintaining a sustained speed of more than 2 million events per second (EPS).
15,000+
Correlation rules defined
COR SIEM provides more than 160 pre-designed correlation rules that fit some of the most common use cases related to malware and credential compromise.

Asset library
-
The asset library (CMDB) offers you an agile and efficient management of your infrastructure components, completely online. In addition, it has all the necessary integrations to interact with your company's CMDB and the most used brands in the market.
Autodiscovery & topology map
-
Experience agile and contemporary search coupled with powerful correlation, detailed reporting, intuitive dashboards and efficient case management. COR's functionality to easily and efficiently design a network dependency topology model will amaze you.

What else can COR do for you?
-
Experience agile, contemporary search coupled with powerful correlation, detailed reporting, intuitive dashboards and effective case management. Don't let your legacy SIEM be a prisoner; set it free with COR SIEM, an affordable, easy-to-implement, easy-to-use solution that your teams will eagerly adopt.
Support
COR’s support team is committed to helping you achieve key business results. We have extensive experience, resources and tools that will support your security team in achieving their short and long term goals.
Services
COR’s professional services empower customers to accelerate implementation, reduce time to value, and take ownership of policy management through a clearly defined framework that offers options for fixed delivery packages or customized services. These services streamline platform implementation, integration and management while ensuring maximized success.
Training
Provide your team with the necessary tools and training required to effectively use the COR security operations platform. Whether through instructor-led training or at your own pace, your employees will learn how to optimize the features and functionality of the COR solution, ensuring they get the maximum value from it.
Partners
COR was established on the fundamental principle of openness. We recognize that our technology and marketing partners play a vital role in our success. Security is a collaborative effort, and our business partnerships are an essential component in ensuring your success.
• Cloud-scale or local data ingestion and monitoring
• Normal reference behavior
• Automatic scoring and profiling of user activity
• Display of predefined incident schedules
• Use strategy manuals to make the next right decision.