Schedule a meeting with a specialist
Agenda una reunión con un especialista
Cybersecurity platform
for the operation and management of
risk management
Different needs, a comprehensive vision.
Although not everyone is looking for the same thing, everyone wants efficient results.
At Camel we know that each role requires different solutions.
Although not everyone is looking for the same thing, everyone wants efficient results.
At Camel we know that each role requires different solutions.

Executive management
Visibility
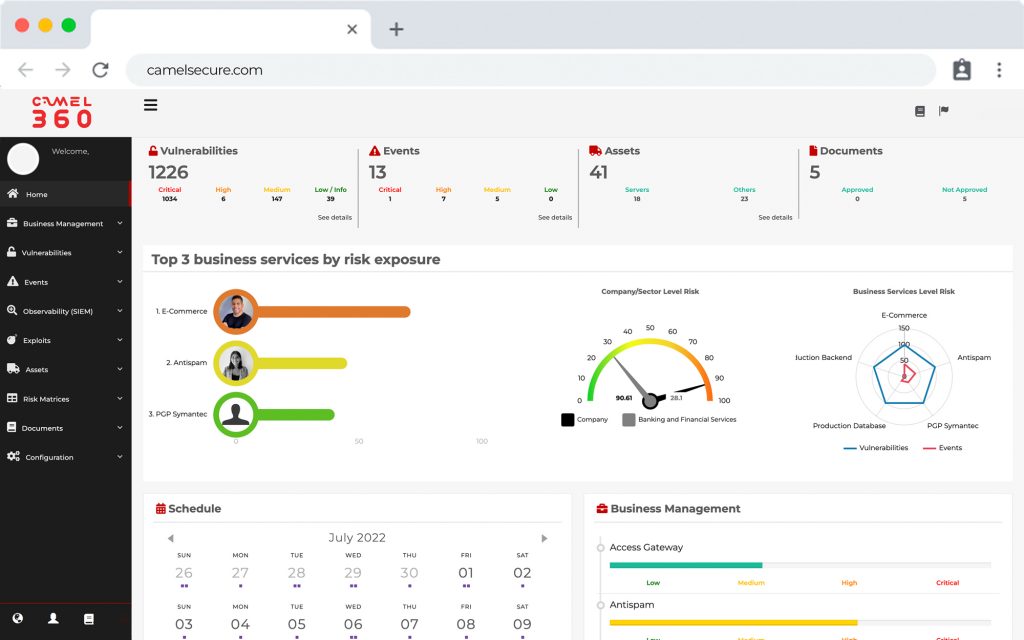
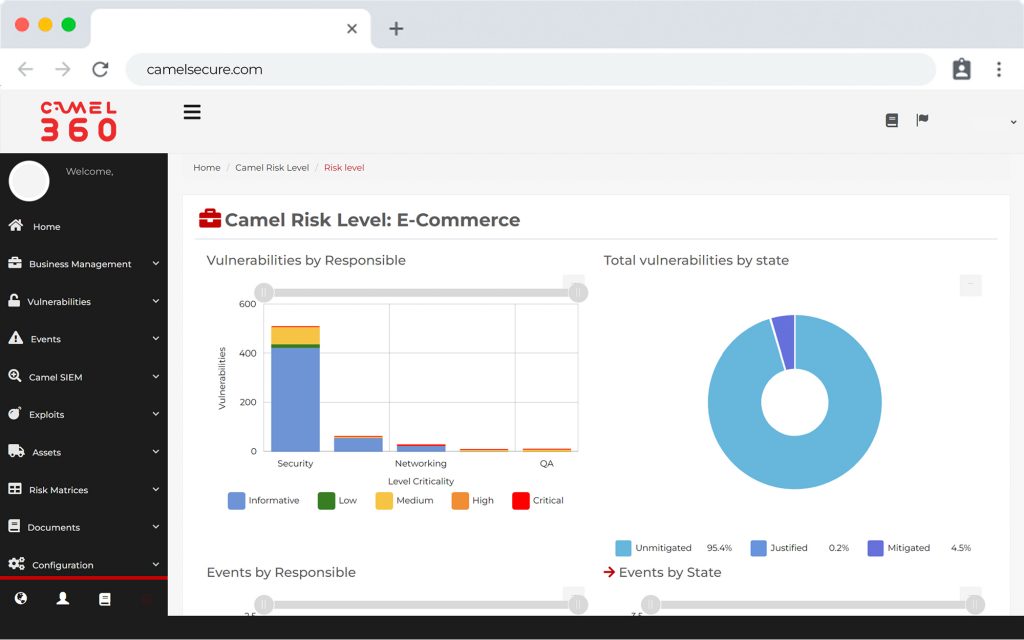
Visualize in real time which of your business services is most affected or most exposed to risk. Be in control and improve decision making.

Leaders in Cybersecurity
Management
Manage and minimize IT risk in your critical processes, all in a single platform. Take control and save the most valuable resource, your time.

Cybersecurity Specialists
Technology
We know that technology moves you. With Camel 360 you can unify, visualize, correlate, detect and automatically respond to all attack activities.
When we tell you that
Camel 360 will make your life
simpler, it's true.
Camel 360 will make your life
simpler, it's true.
Efficient management of
your cyber risks starts
with CAMEL 360
We give you complete and continuous visibility
continuous visibility of your operational risk.
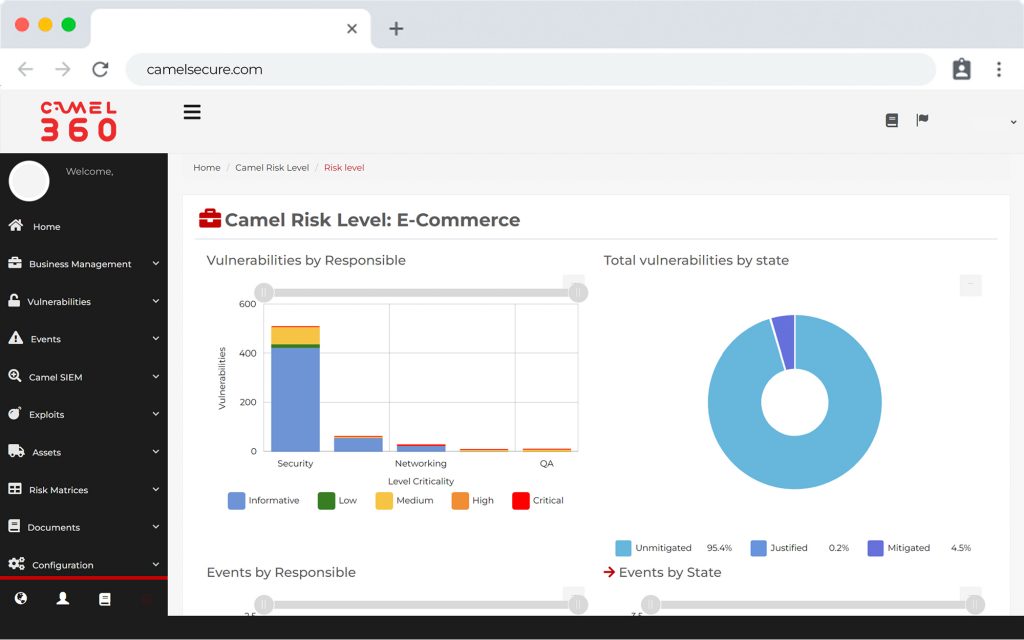
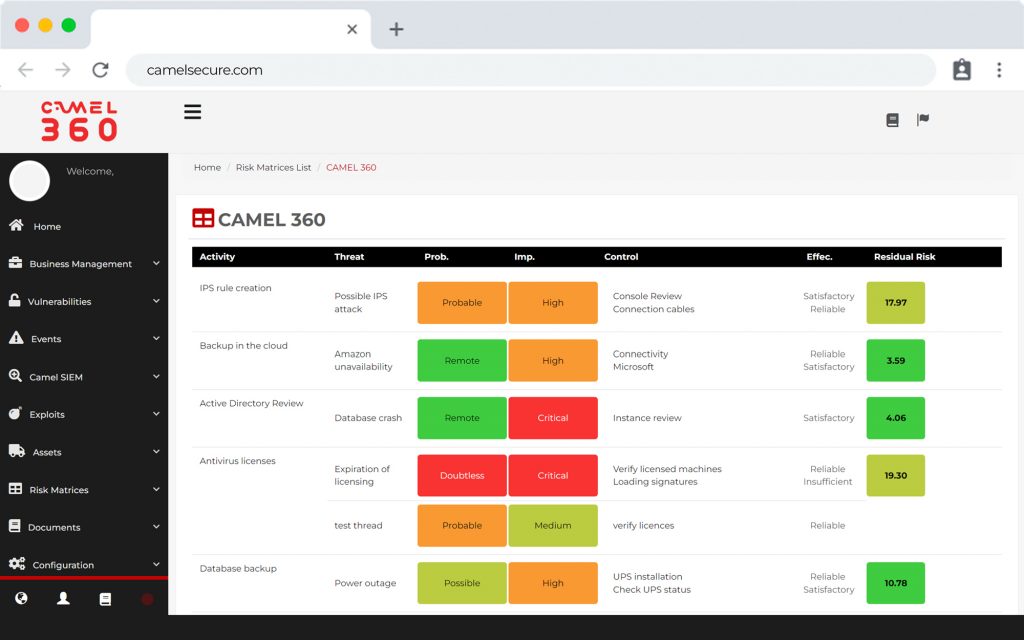
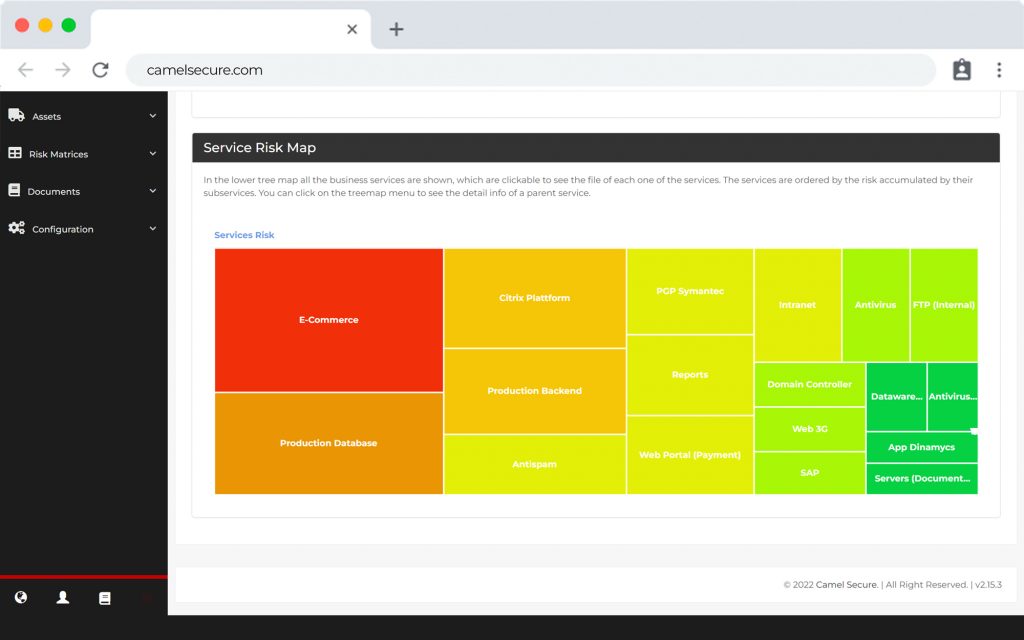
Visualize the technological risks of your business services and manage the assignment and remediation of threats plus an artificial intelligence component that learns from patterns and automates responses, all from a centralized 24/7 online dashboard.
With CAMEL 360
Close your risk gap
with total visibility
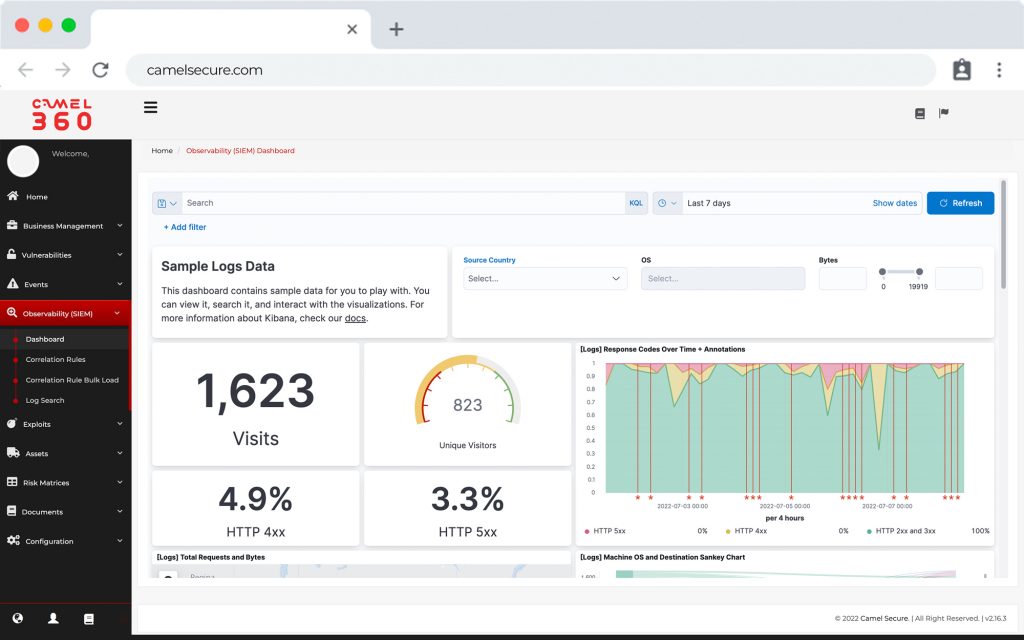
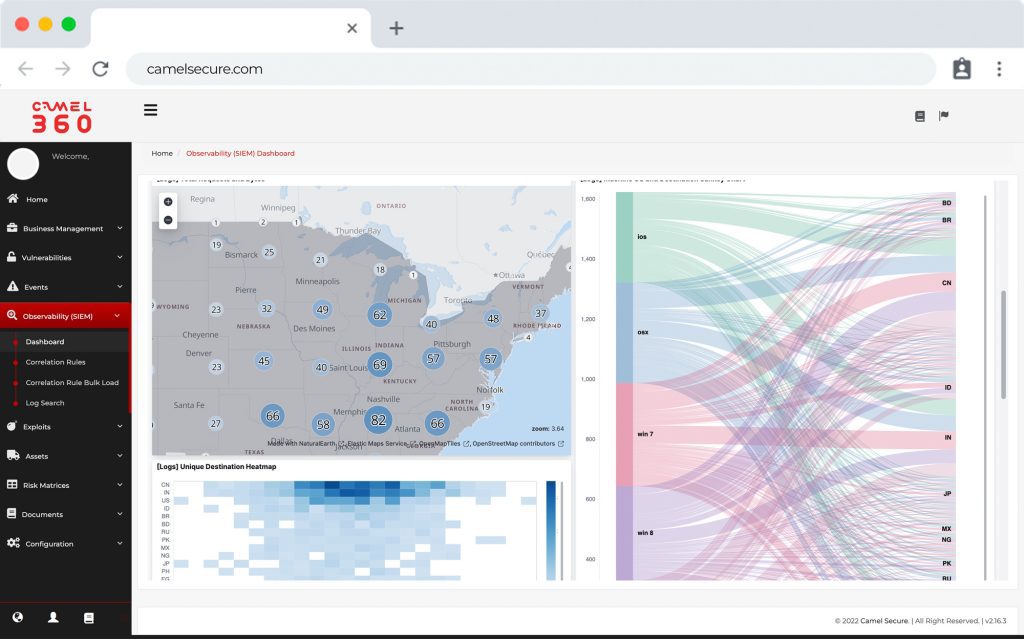
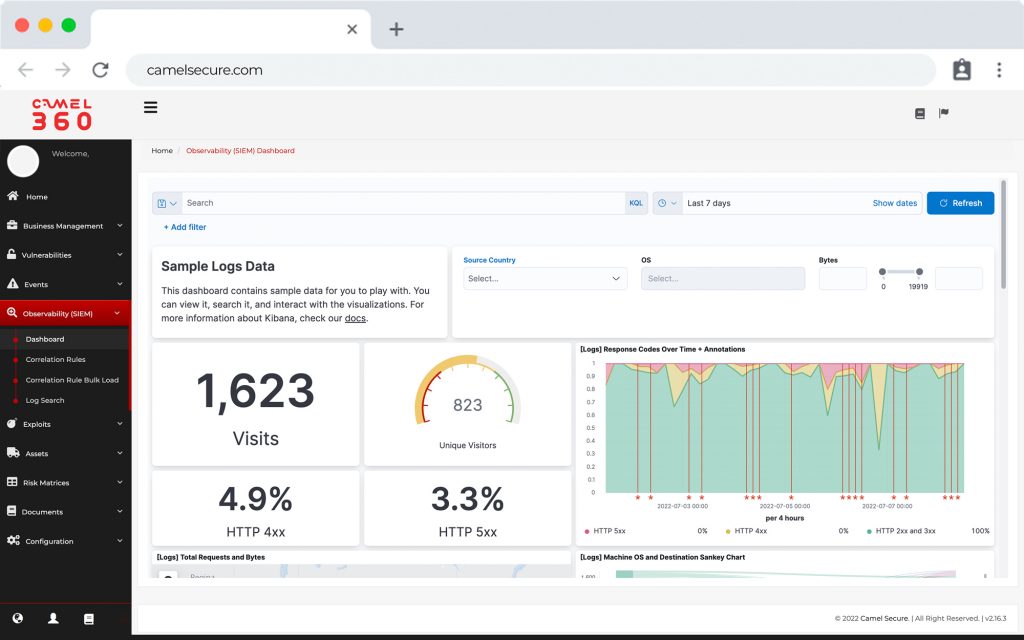
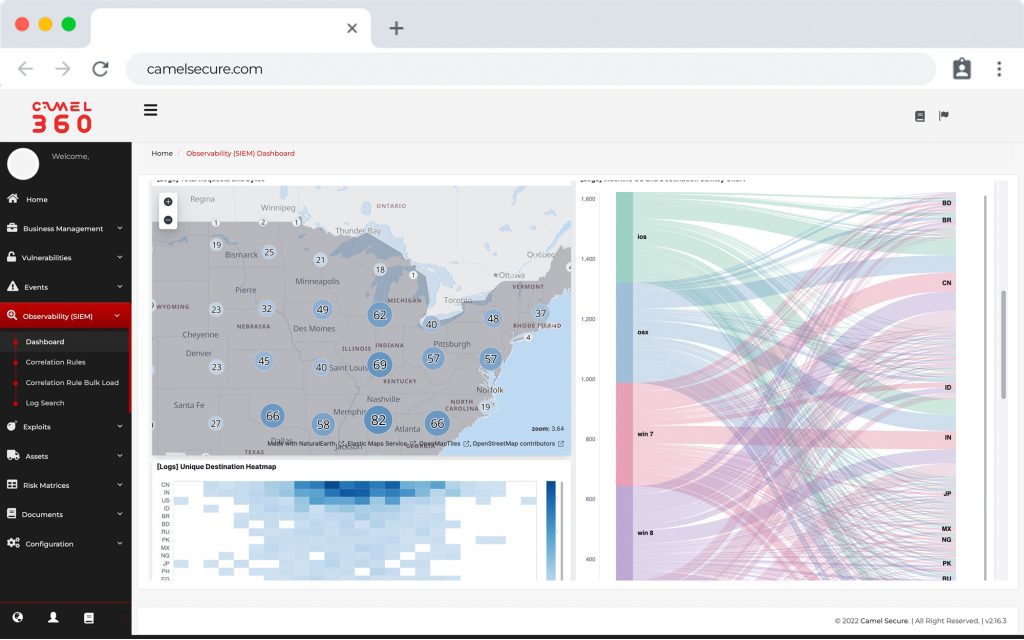
Camel SIEM
Allows agnostic integration with different infrastructure components, perform behavioral patterns or emulate a hacker attack. Camel SIEM belongs to a new and exclusive generation of “SIEM event correlation”, oriented to visualize the technological risk from the perspective of your business, leaving behind the traditional way of monitoring risk depending on the criticality of the events of your infrastructure.
Correlation strategies
Our correlation rules are based on MITRE ATT & CK®. Which is a globally accessible knowledge base of adversarial tactics and techniques based on real-world observations. The ATT & CK knowledge base is used as the basis for the development of specific threat models and methodologies in the private sector, government and the cybersecurity products and services community.
Camel 360, the cybersecurity suite with the most advanced technology in technology risk management.
Classify, organize and manage your business services, with Camel SIEM, Incident, Vulnerability manager, CMDB and Document Risk IA. All with an approach close to the business.
We modernize the
Infrastructure analysis
Maximize your efficiency by mapping your
business services on the infrastructure
infrastructure and assets.
Maximiza tu eficiencia mapeando
tus servicios de negocios sobre la
infraestructura y activos.
CAMEL 360 identifies, manages and calculates technology risk with a modern approach that will change your life.
The benefits
of modern
modern management of
cyber risk management
Services focused on your business
CAMEL 360 is the most suitable tool for organizations and security consultants.
Link the threats
with the impact to platforms and
platforms and operations.

Visibilize the impact to your company’s lines of business.

Centralizes the entire
infrastructure and associates
to the different business
services, whether IT or OT.

Allows you to generate customized risk
customized risk maps
for each company.