Schedule a meeting with a specialist
Agenda una reunión con un especialista
Are you facing a new project
project and think that your
infrastructure might be vulnerable?
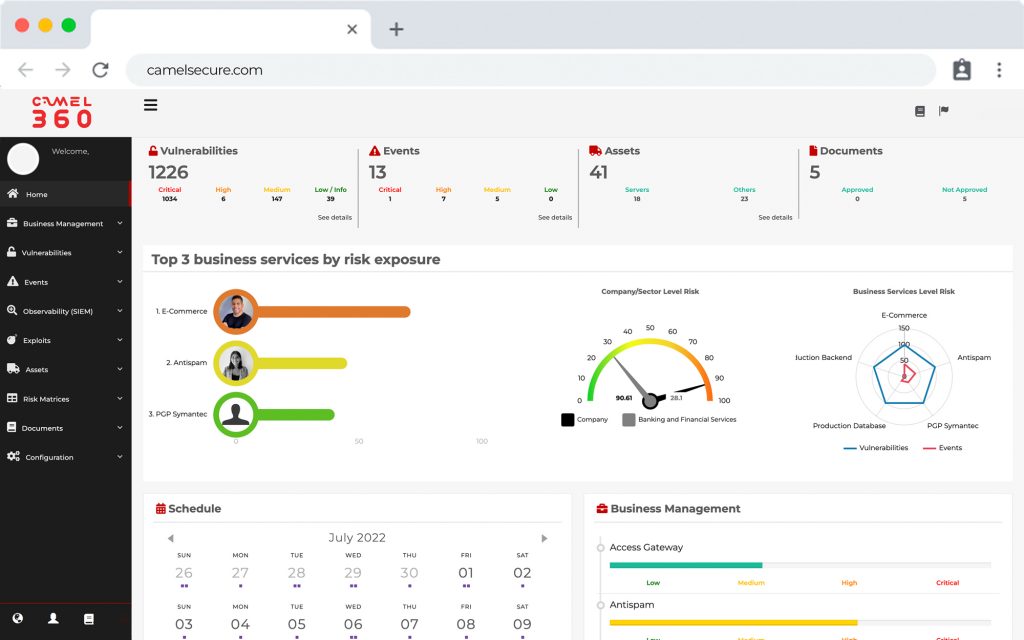
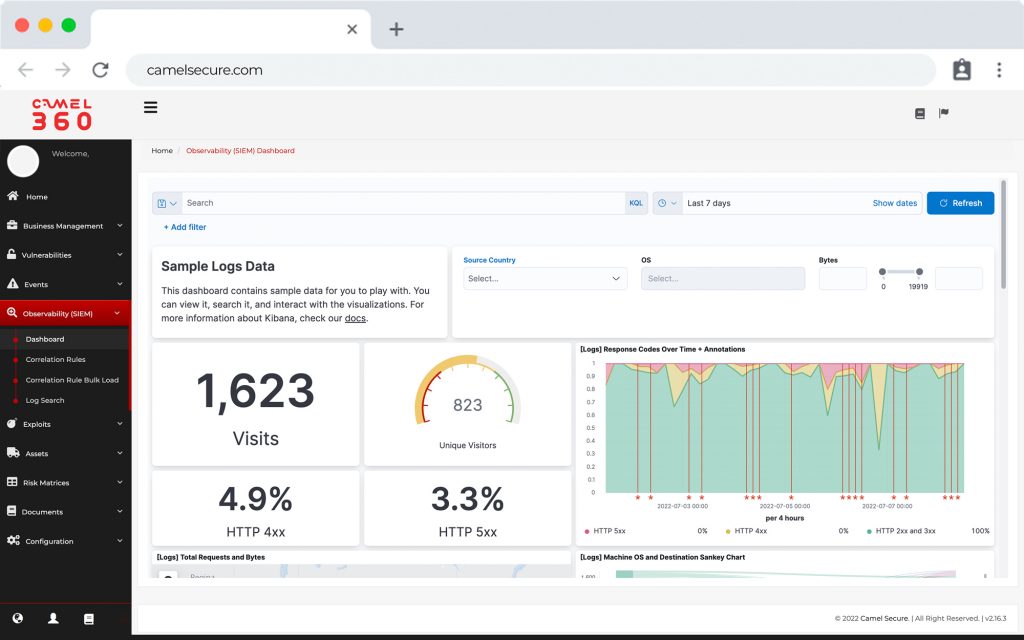
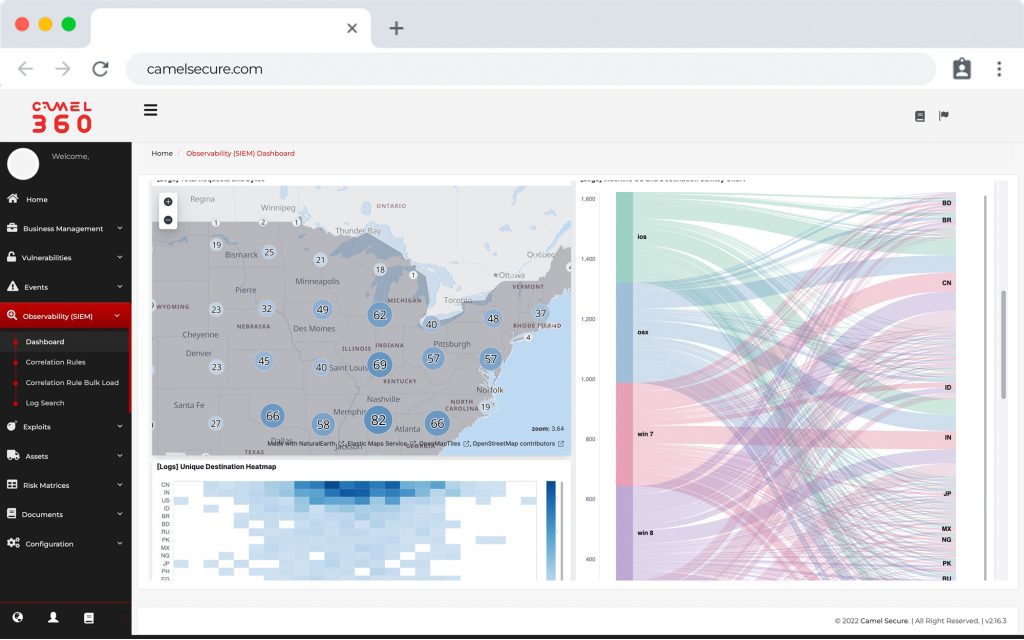
CAMEL X, is a powerful tool and exclusive generation of “Vulnerability Scanners”, which is focused only on infrastructure vulnerabilities (IP analysis), in addition to using the traditional way of visualizing vulnerabilities, allows organizations to have a CMDB with multi-classification and auto-discovery, thus keeping the infrastructure of organizations updated in real time, informing changes in the ecosystem formed by the production areas of each company.
Create your own library
infrastructure library
is now easy
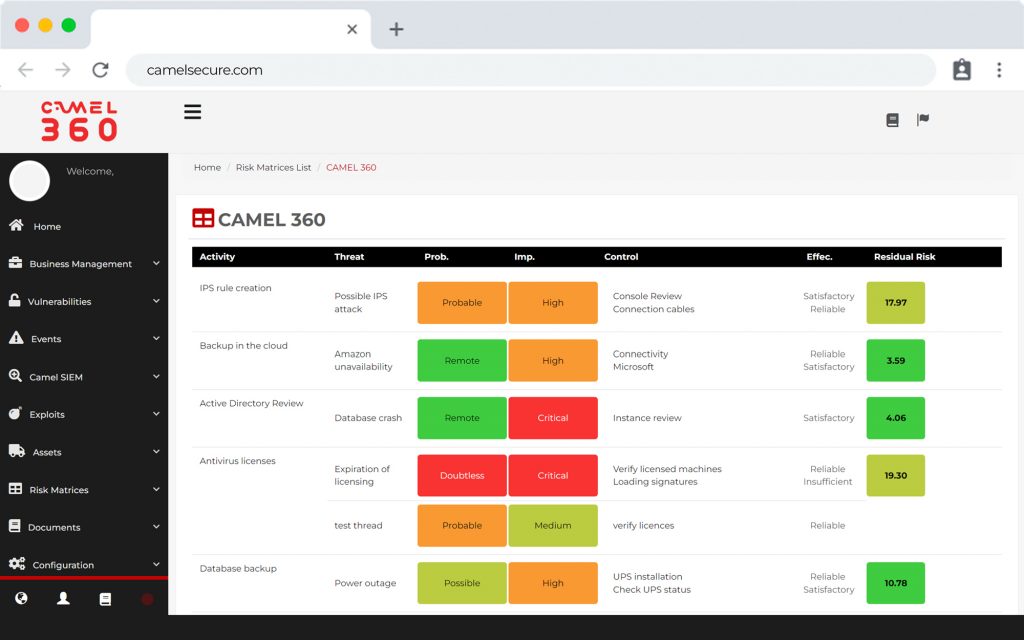
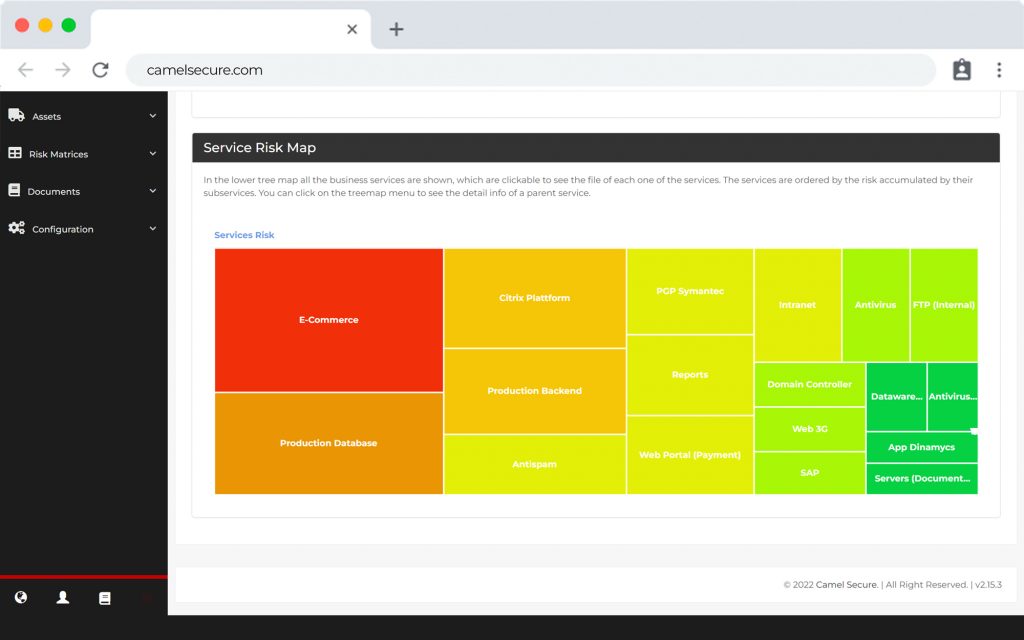
CAMEL X has a multi-classification CMDB, which allows you to create infrastructure components with the particular configuration of each component and for each business. CAMEL W can create, reuse or choose fields of use in each infrastructure file, allowing you to create automatically and without human intervention all the dashboards that the organization requires, in a user-friendly way and enhanced with the auto-discovery and management functionalities, already included in the license of use.
Camel Exploits
Camel X has an exploits module to proactively help users by automatically identifying all the exploits or zero days that have been raised in the last hours worldwide and that could affect the client’s infrastructure. Don’t worry if you can’t run vulnerability scans every day, with Camel Exploits you will be able to know if there are threats that could affect. Our message is, let’s stop being reactive and be more proactive.

More automation,
less hassle
ADVANCED CUSTOMIZATION
Allows access to the most advanced vulnerability scanning technology.
vulnerability scanning technology, with CAMEL X you will be able to
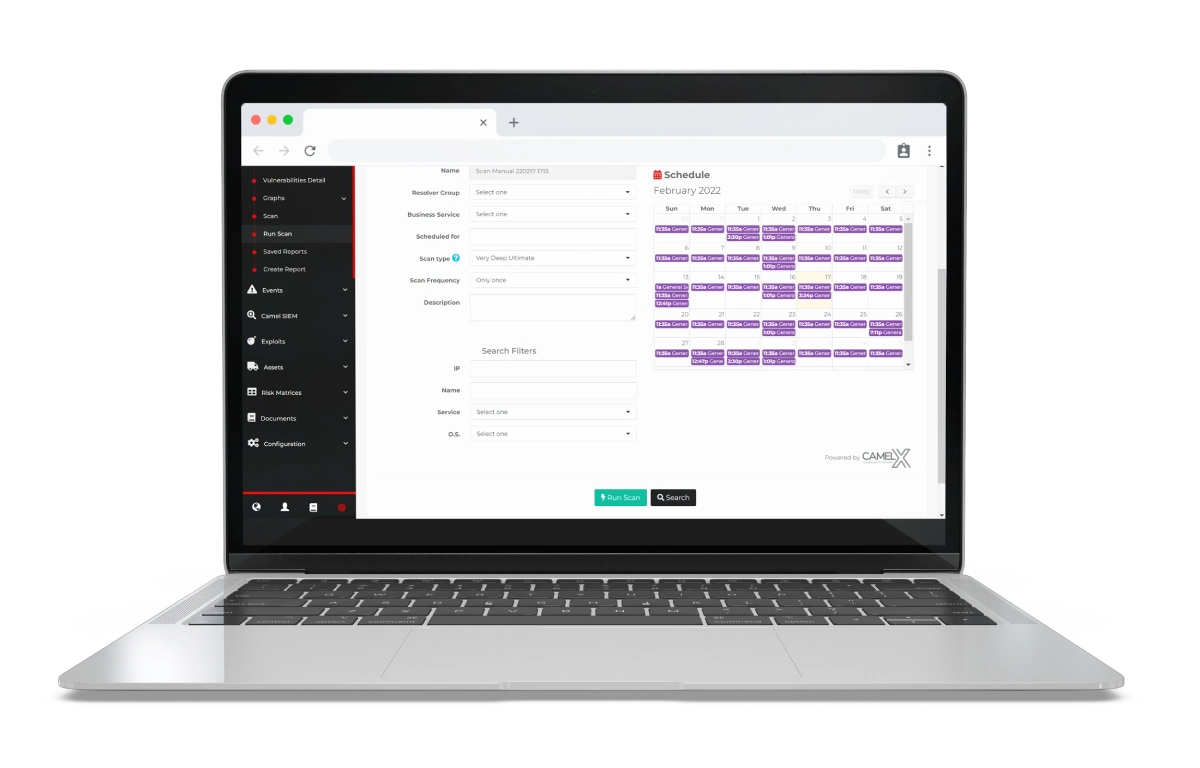
Schedule multiple scans
Vulnerability mapping by
technology or operating system
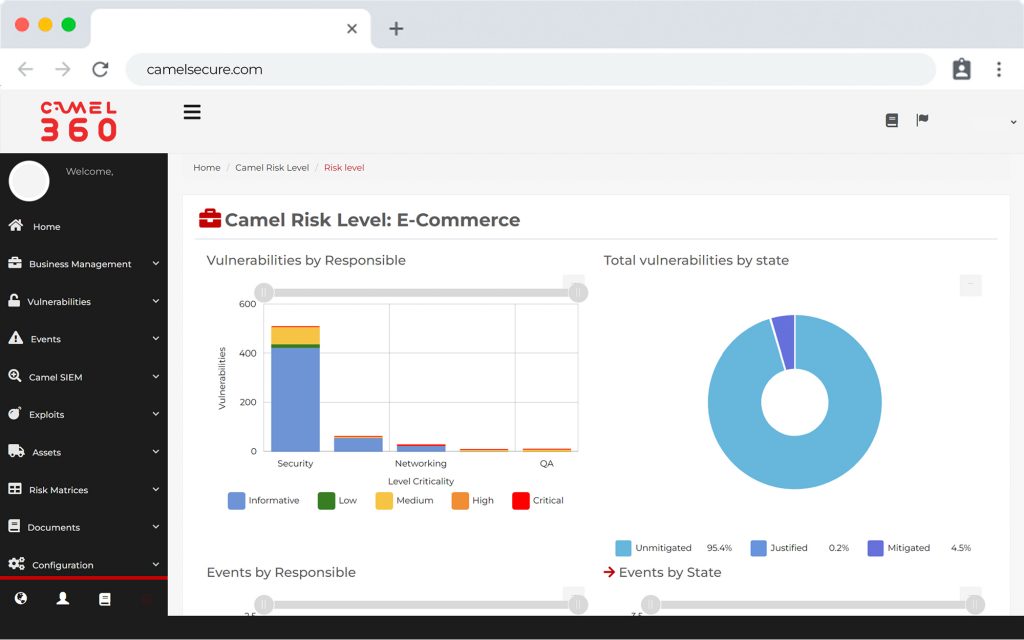
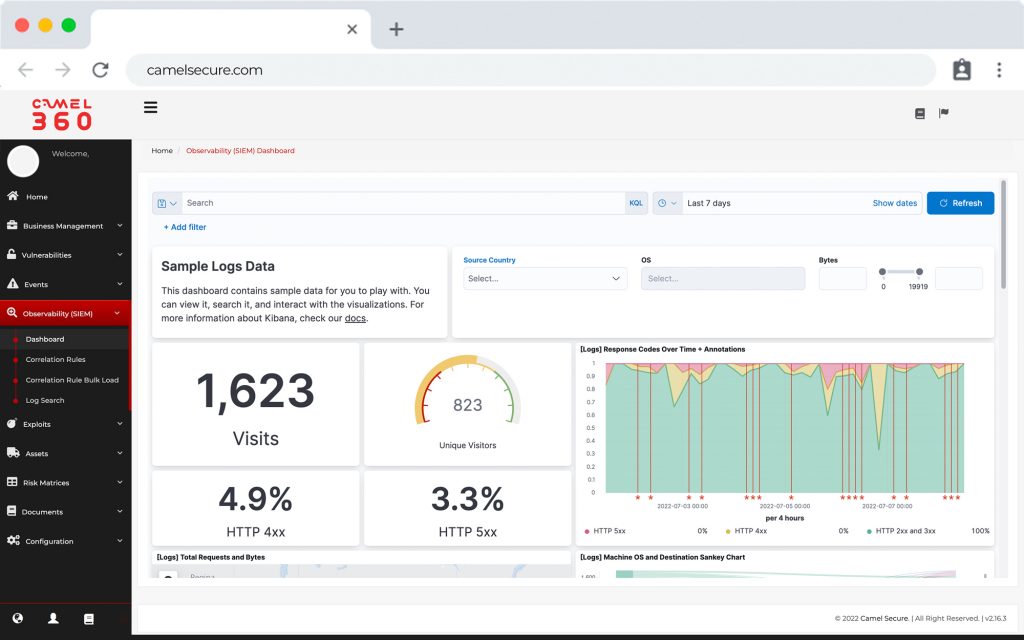
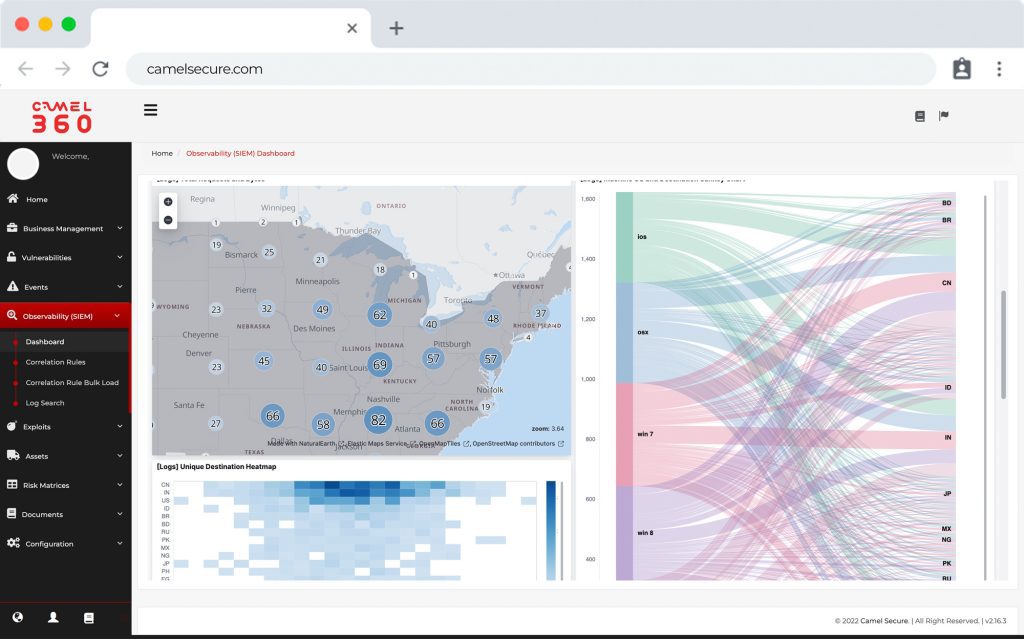
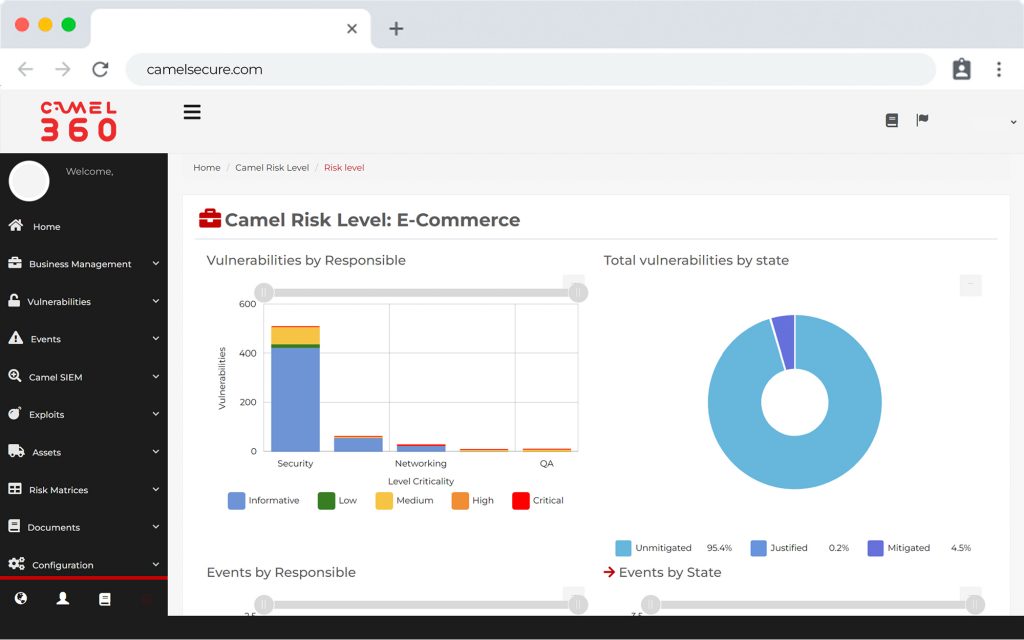
View operational and executive
Operational and executive dashboards
Artificial intelligence for vulnerability vulnerabilities according to OWASP
CAMEL X , a powerful tool and the most suitable one for organizations and security consultants
SUPPORT
ADVANCED
Access through our “CAMEL COMMUNITY” platform to our various professionals in the region, allowing queries related to CAMEL W or related products, such as CAMEL X, Camel W or CVM, via forums, email, chat or phone.
CAMEL X
IS AGNOSTIC
Allows you to interact and report security breaches from the integration of the four main modules of the platform: Vulnerabilities, Incidents, Assets and Documentation.
THE SECURITY
OF CAMEL
CAMEL X has the highest security standards, controlling point-to-point connectivity through SSL, AES-256 encryption, two-factor authentication, WAF, Security Group and controlled access lists.