[rev_slider alias="home-2022-v4-en"]
Who is Camel Secure?
Camel Secure is the only cybersecurity suite, which has all the necessary technology to accompany your operation process and technological risk management.
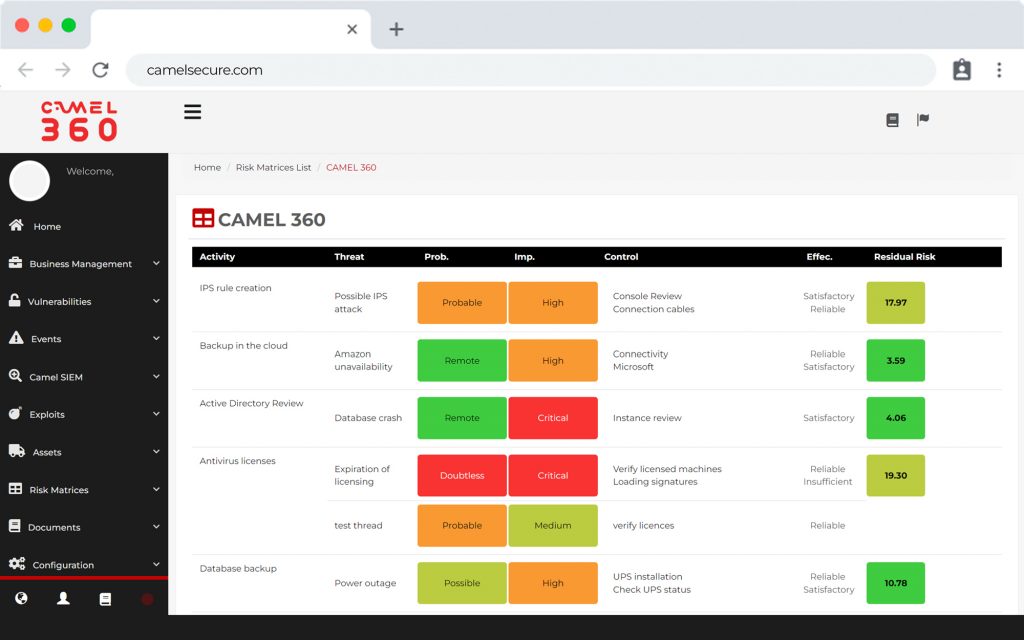
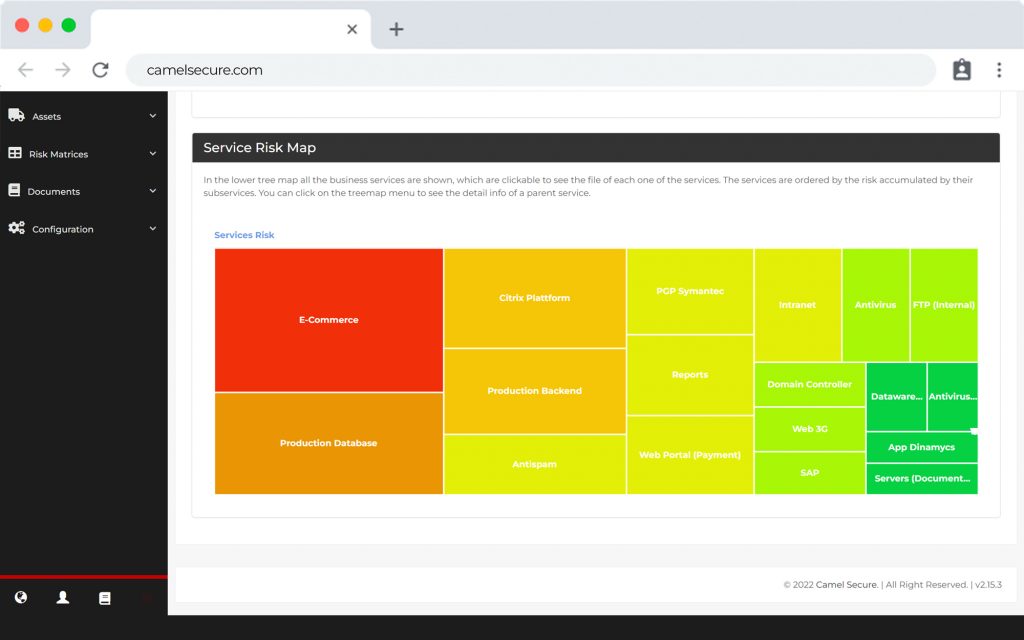
Among the functionalities of our platform are included: SIEM, Analysis and management of vulnerabilities operation, Management and calculation of IT risk, Library and discovery of assets, Heat maps or Risk Matrices.
All this in Service as a Service (SaaS) mode. This allows the necessary flexibility for rapid acquisition and implementation.
Among the functionalities of our platform are included: SIEM, Analysis and management of vulnerabilities operation, Management and calculation of IT risk, Library and discovery of assets, Heat maps or Risk Matrices.
All this in Service as a Service (SaaS) mode. This allows the necessary flexibility for rapid acquisition and implementation.
[display-map id='16027']
¿Quien es Camel Secure?
Hoy contamos con presencia en USA y Latinoamérica gestionando el riesgo tecnológico de importantes Empresas de forma agnóstica y transversal.
Camel Secure es fundada en 2018 por un equipo de expertos en Cybersecurity y desarrollo de sistemas críticos.
[display-map id='16027']
Large customers support us.

















Previous
Next
Management
and analysis of
vulnerability
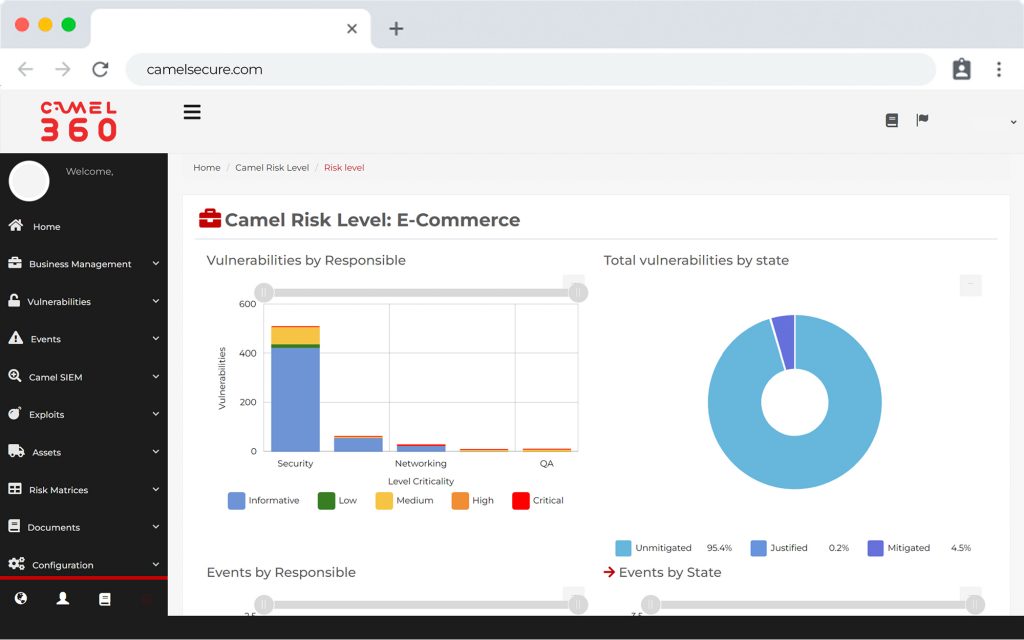
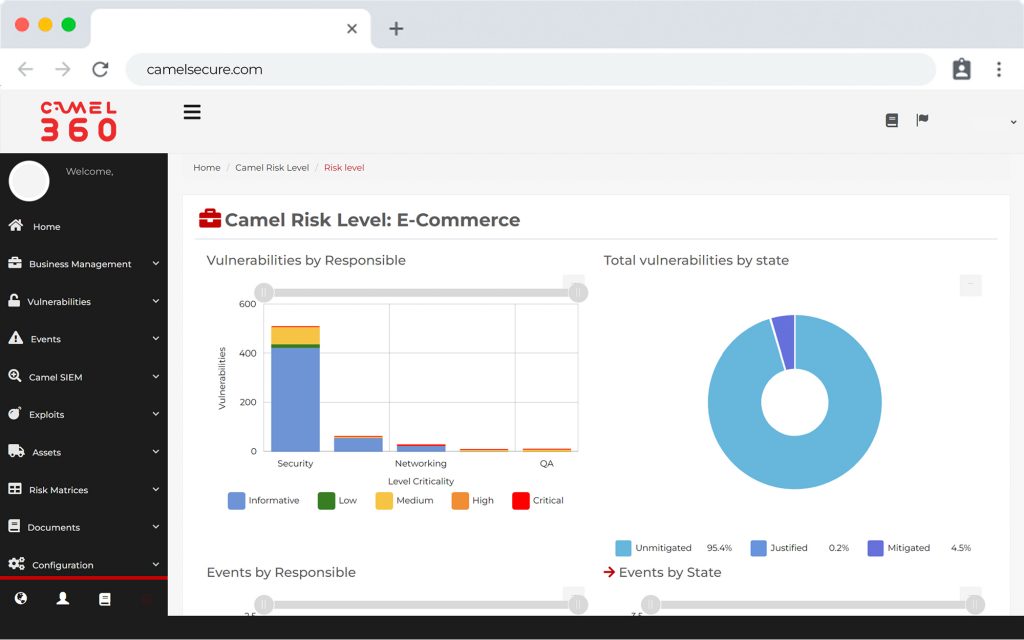
CVM is a product that belongs to a new and exclusive generation of “Vulnerability Manager”, oriented to visualize and manage the technological vulnerabilities of organizations from the perspective of their business, leaving behind the traditional way of calculating the risk depending on the criticality of the vulnerabilities of their infrastructure.
.

Vulnerability management based on assignment to resolution groups.

Automatic calculation of compliance SLAs.

Self-discovery of infrastructure and proprietary CMDB.

Analysis of infrastructure and web vulnerabilities on a single platform.

One control panel.
Many possibilities.
We calculate the cyber risk of your business.

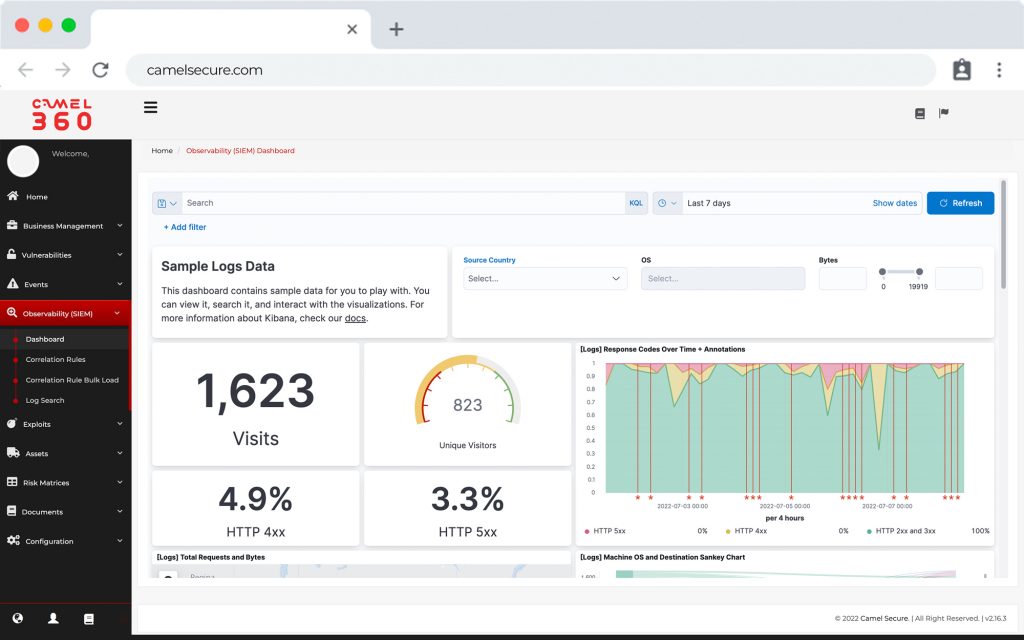
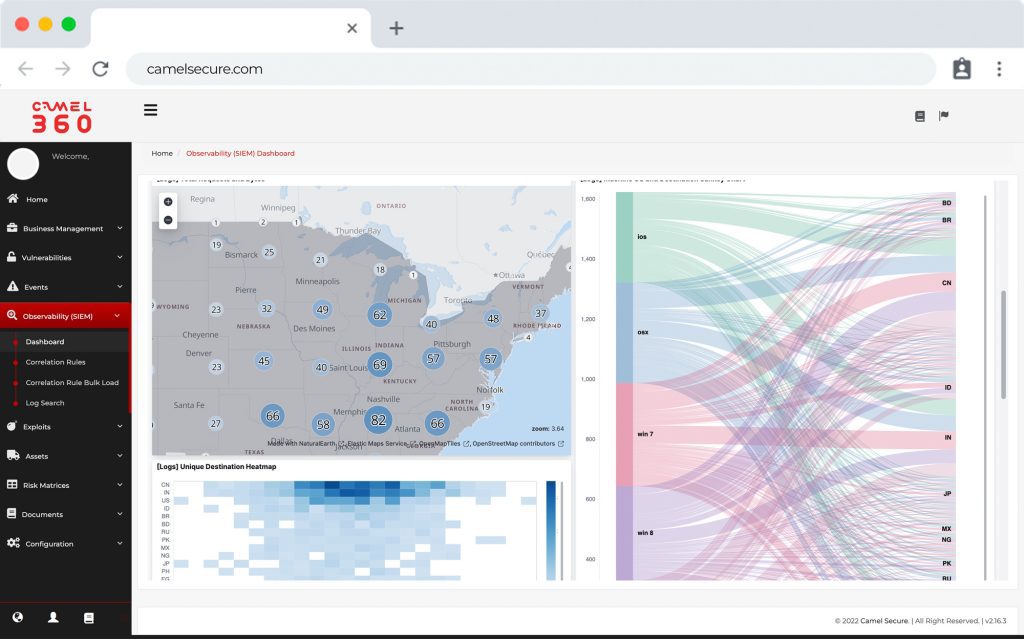
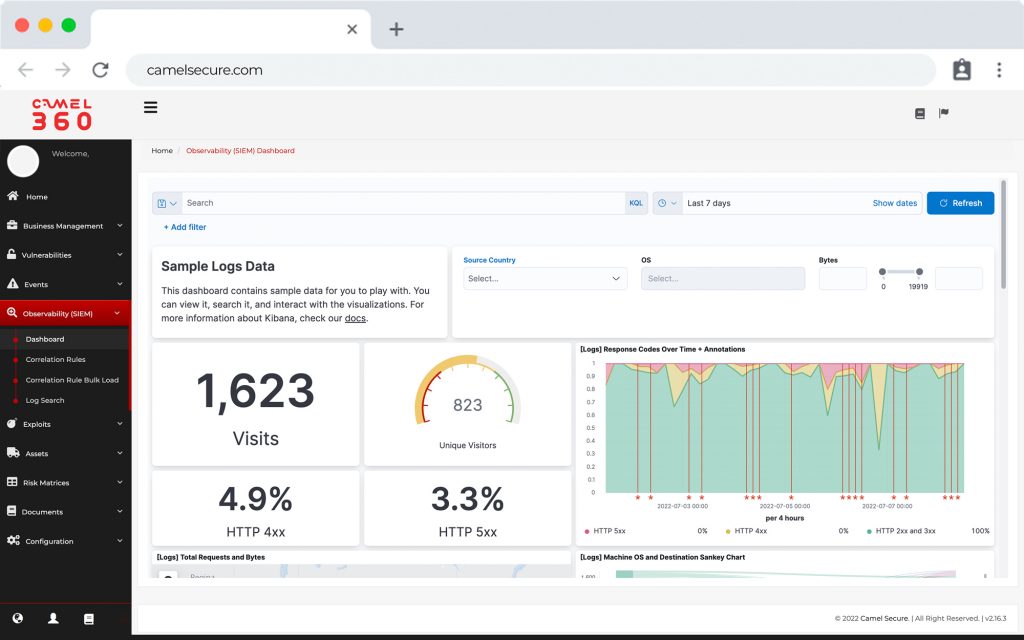
Operations intelligence
Real-time monitoring and troubleshooting
Increase efficiency in problem resolution. Camel helps you reduce your cybersecurity gap and move from reactive to proactive monitoring with a SaaS service mode for rapid acquisition and implementation.

Security intelligence
Respond to threats immediately
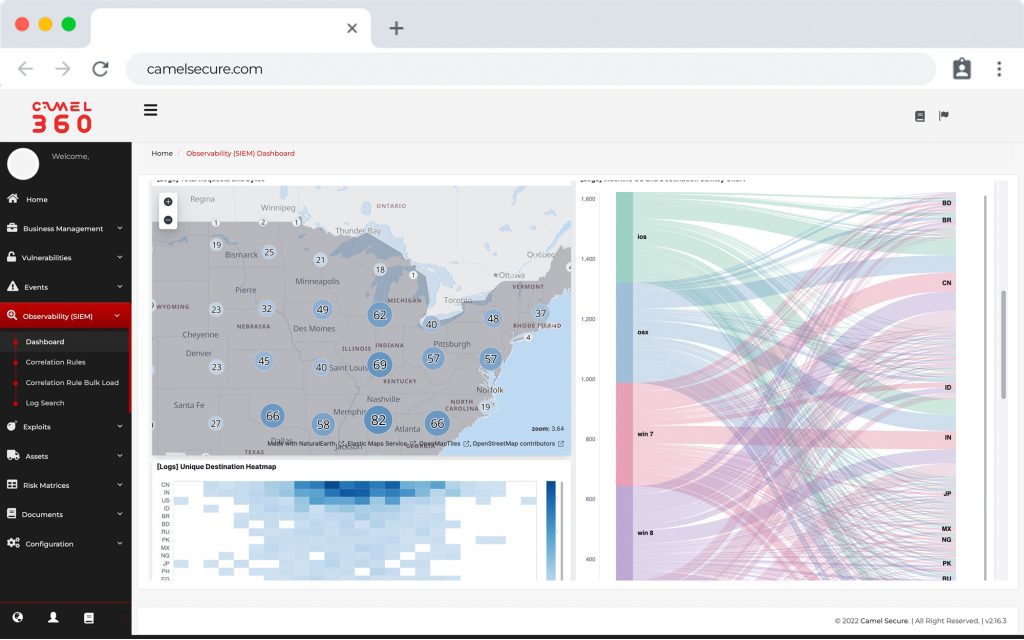
Quickly detect threats with our SIEM, analyze and manage vulnerabilities and ensure their elimination using Camel Secure.

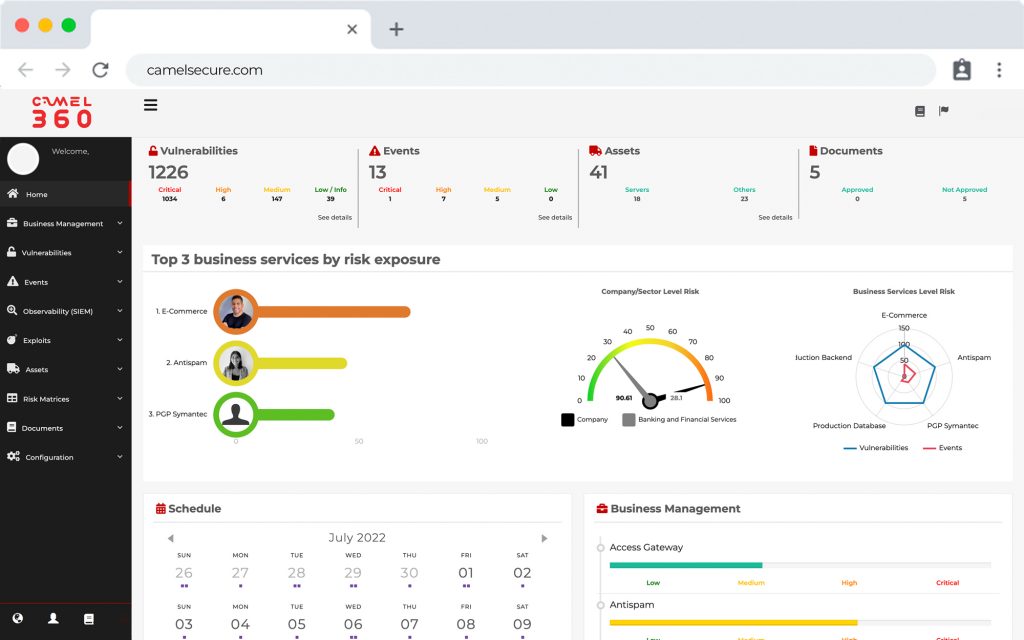
Business intelligence
Make better decisions
Enable data-driven business decision making with our risk matrices or heat maps of your business.
Virtual intelligence
Continuous, cloud-native cybersecurity platform
It adapts to your infrastructure and assets, regardless of the size of your company.
Full control.
A central panoramic
view.
A powerful platform that includes everything you need for IT Risk Management; SIEM, Vulnerability manager, Asset Discovery, Incident response, Compliance and much more.
We transform millions of data into important information for your company.
We facilitate the visualization of your cybersecurity activity with quality information through an intelligent and centralized platform. While our specialists accompany you in your risk management with our SOC aaS managed service.