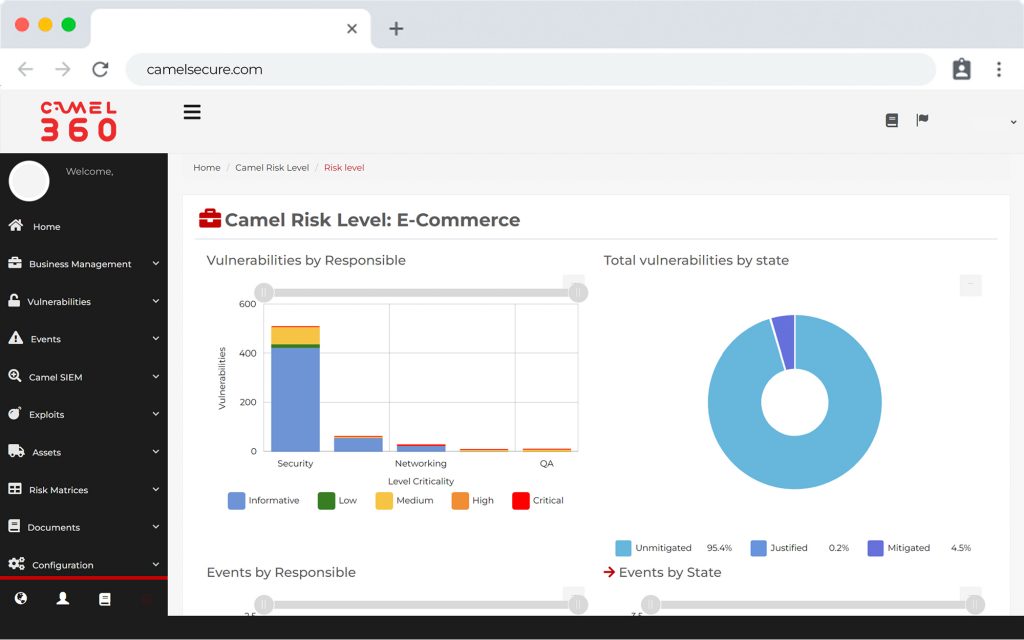
Vulnerability analysis and management
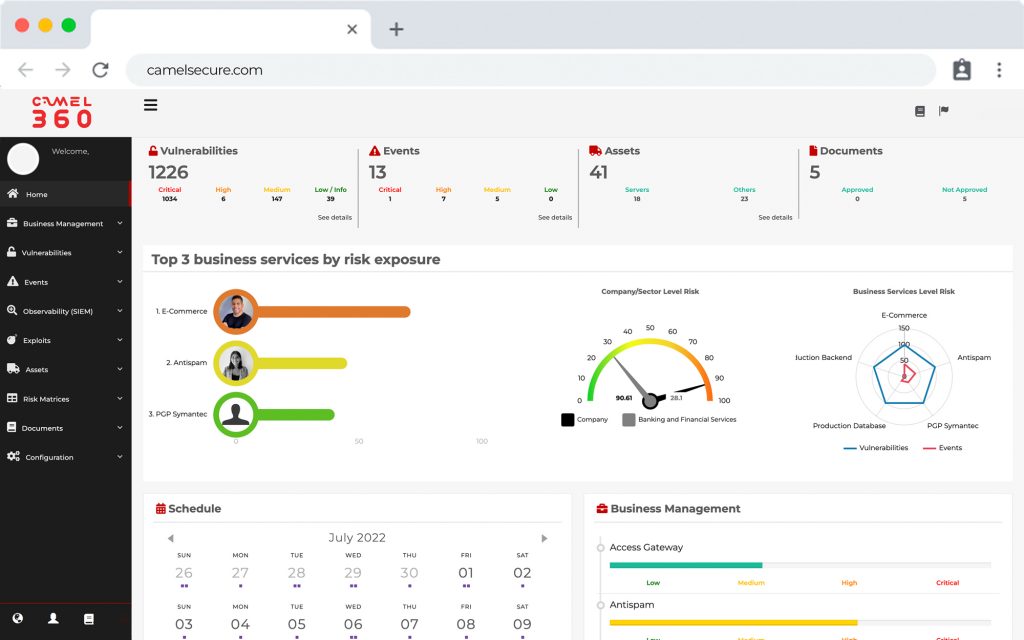
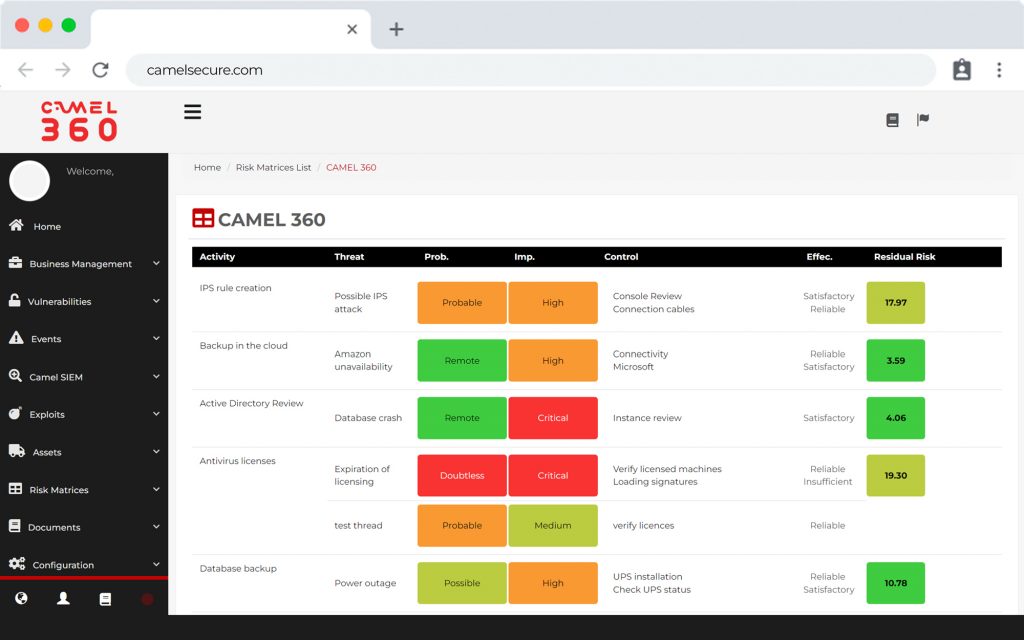
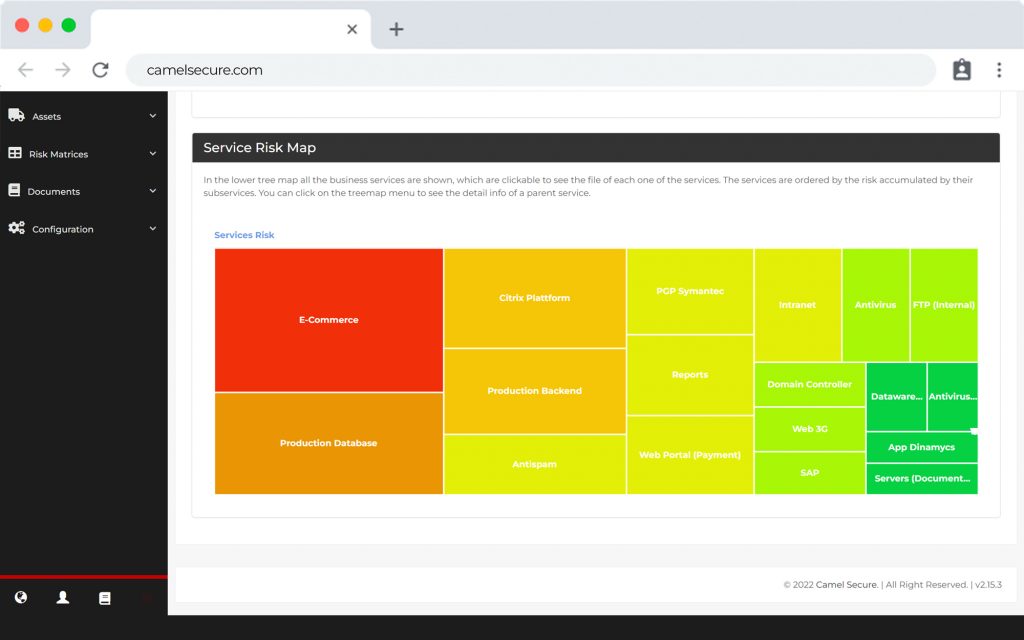
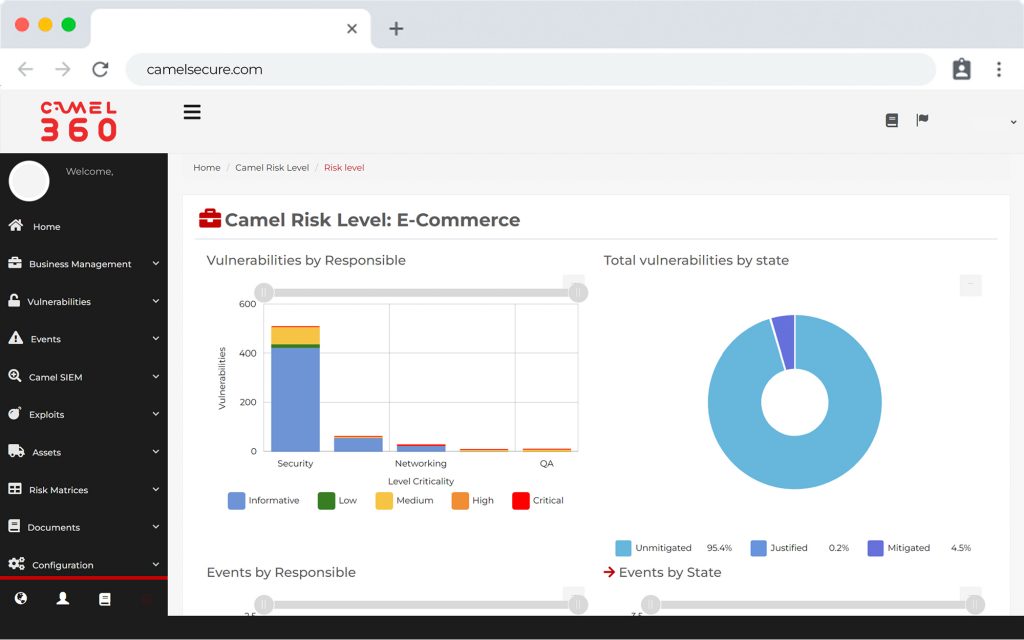
The first software that allows you to integrate vulnerabilities from multiple platforms and manage them in a central dashboard with a risk and business view.
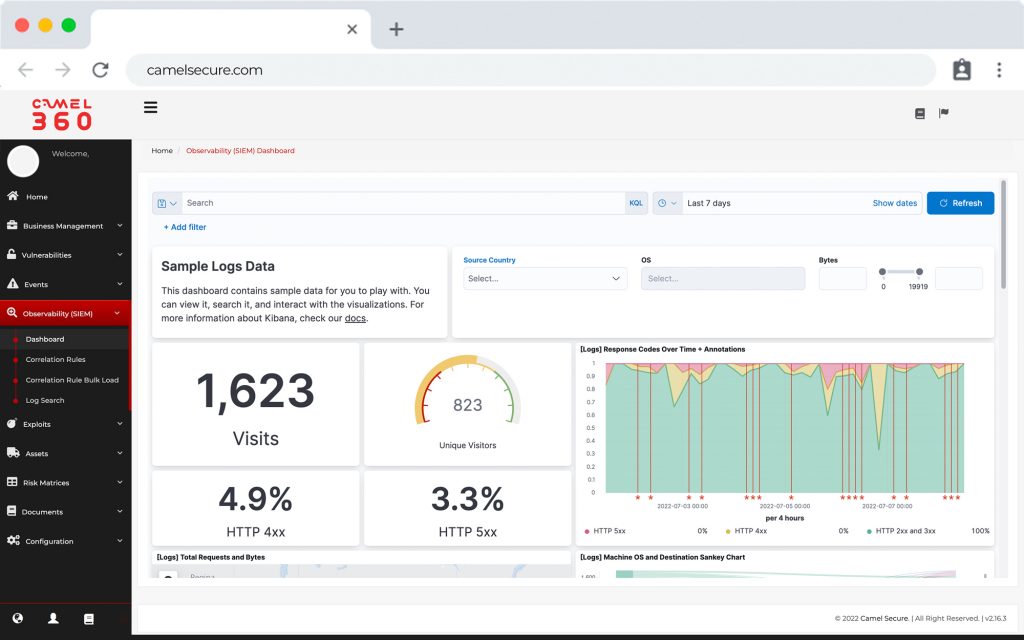
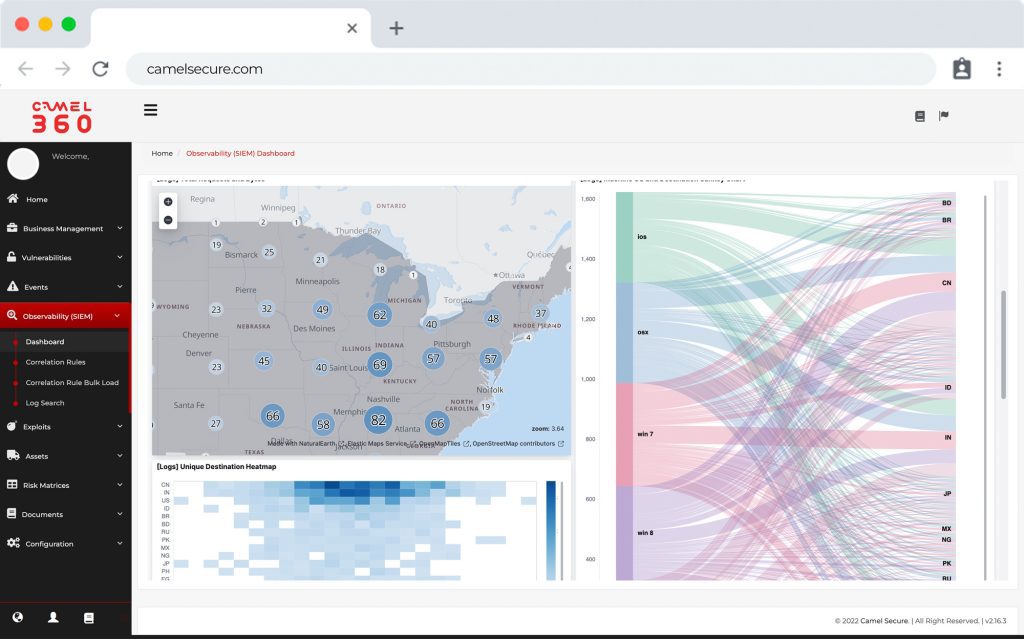
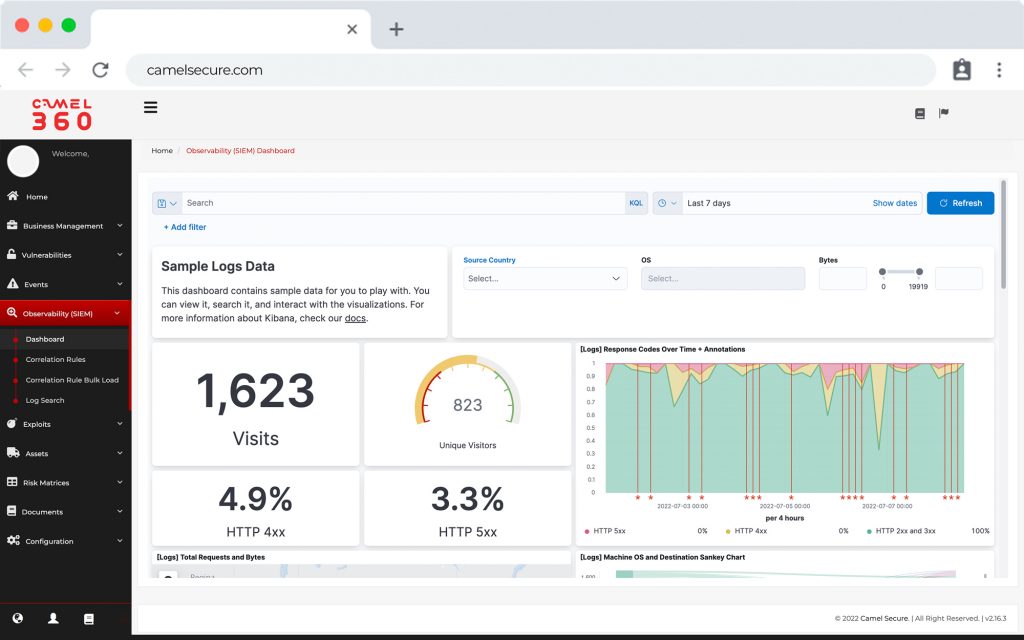
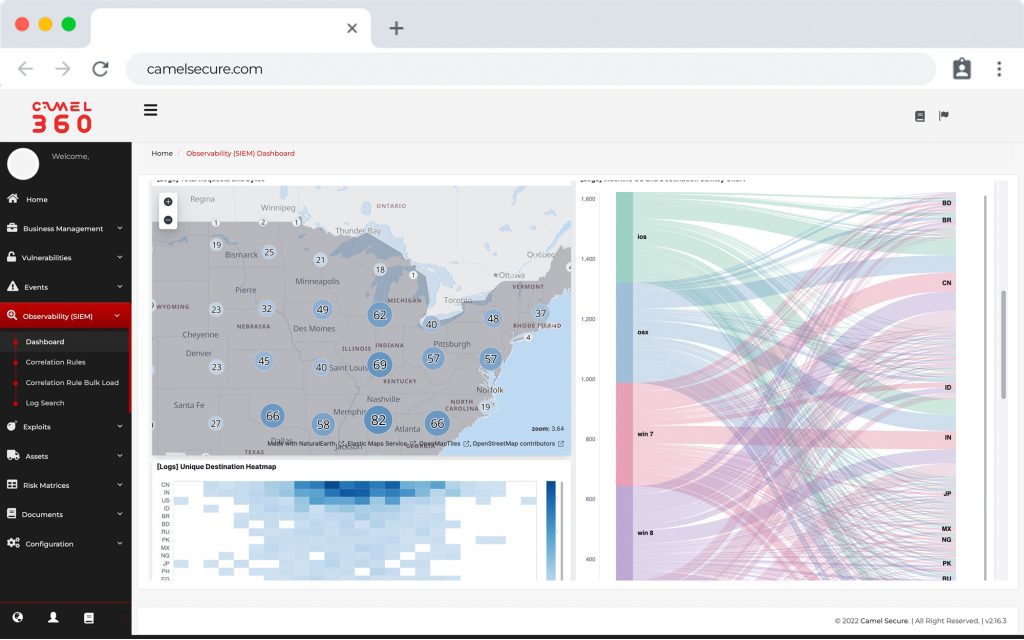
Observability and Reponse
Cloud-native observability software designed for hyperscale, with fast, modern search and powerful correlation. Offers detailed reports, advanced dashboards and efficient case management tools.
API Vulnerability Manager
Your APIs are undergoing changes all the time, even without your knowledge. Plugins are being updated, different users are logging in to make edits, and the systems your site uses are also being modified.